Table of Contents
Vulnerabilities
Vulnerabilities are weaknesses or flaws in a system, network, application, or process that can be exploited by a threat actor (such as a hacker) to gain unauthorized access, disrupt services, or compromise data.
What is Vulnerability?
Answer: Weakness in an information system, system security procedures, internal controls, or implementation that could be exploited or triggered by a threat source.
Types of Vulnerabilities?
3: Security Weaknesses:
1: Common Vulnerability and Exposure (CVE).
2: Misconfigurations.
3: Mismanaged Credentials.
4: Unmanaged Infrastructure (Shadow IT).
Common Vulnerabilities and Exposures
1: Microsoft Office ASLR Bypass CVE-2016-0012
Description
Microsoft Office 2007 SP3, Excel 2007 SP3, PowerPoint 2007 SP3, Visio 2007 SP3, Word 2007 SP3, Office 2010 SP2, Excel 2010 SP2, PowerPoint 2010 SP2, Visio 2010 SP2, Word 2010 SP2, Office 2013 SP1, Excel 2013 SP1, PowerPoint 2013 SP1, Visio 2013 SP1, Word 2013 SP1, Excel 2013 RT SP1, PowerPoint 2013 RT SP1, Word 2013 RT SP1, Office 2016, Excel 2016, PowerPoint 2016, Visio 2016, Word 2016, and Visual Basic 6.0 Runtime allow remote attackers to bypass the ASLR protection mechanism via unspecified vectors, aka “Microsoft Office ASLR Bypass.”
Buffer Overflow Vulnerability
What is Concurrency?
Answer: Concurrency means executing different parts of a program simultaneously without affecting the actual outcome.
What are Concurrency parts?
Answer: Multiprocessing and Multithreading
What is the difference between Multiprocessing and Multithreading?
Answer: Multiprocessing uses multiple CPUs to execute the information.
Multithreading uses the same CPU to execute the info.
What is Scheduling?
Answer: Scheduling is the arrangement of all the threads to be executed in sequence.
Where can you look for it?
1: Transaction steps.
2: Coupon code.
3: Redeem code.
4: Following user.
5: Liking videos.
What is Clickjacking?
Answer: Clickjacking is an art of social engineering in which a normal user is tricked into clicking and their clicks are hijacked by a tacker without their permission anonymously.
Examples of Clickjacking!
1: Facebook likes jacking.
2: Files Jacking.
3: WebCam Jacking.
4: Follows Jacking.
Dangers of Clickjacking?
1: A hacker can hijack your clicks.
2: By Hijacking, he can open your webcam.
3: By hijacking, he can hijack Facebook likes.
4: By Hijacking, he can hijack Twitter followers.
Authentication-based Vulnerability
An authentication-based vulnerability refers to a weakness in the process of verifying a user’s, device’s, or system’s identity.
These flaws allow attackers to bypass login systems, impersonate users, or gain unauthorized access to sensitive resources.
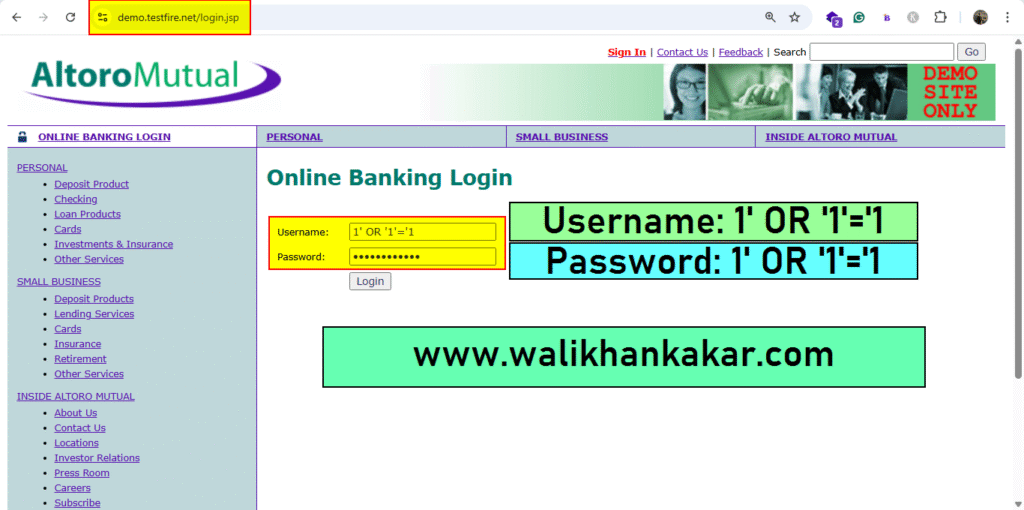
1: Open the TestFire website for testing.
Website: https://demo.testfire.net/login.jsp
2: Try this Syntax.
Syntax: 1′ OR ‘1’=’1