Table of Contents
App penetration testing
Mobile App vulnerabilities
1: DEBUG mode is ON (android:debuggable= “true”)
Mobile device testing
1: Download the SDK Platform-Tools for Windows.
Website: https://developer.android.com/tools/releases/platform-tools
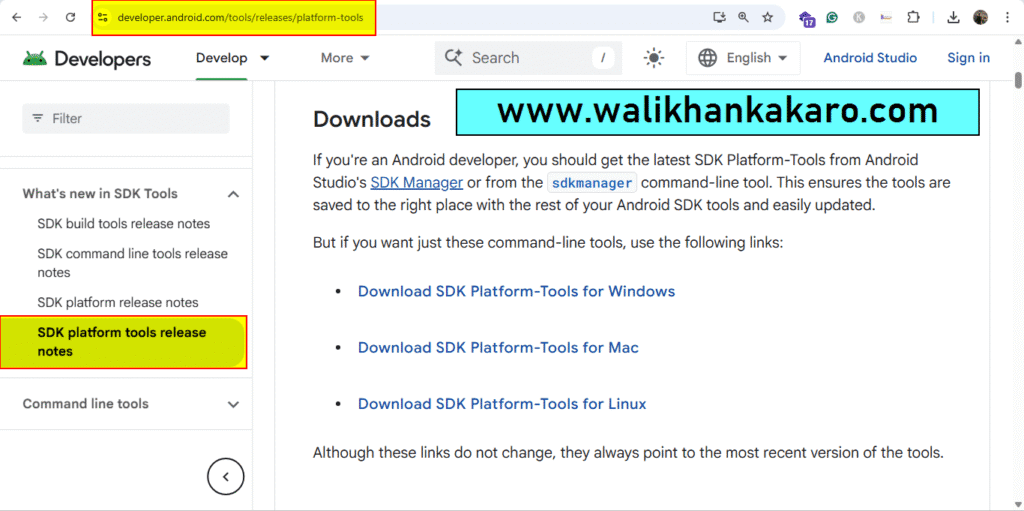
2: Extract the SDK Platform-Tools folder.
3: Rename the platform-tools-latest-windows to the adb.
4: Cut the adb folder and paste it into the Disk C (Where Windows is installed).
5: Connect your mobile to your computer.
6: Enable the USB debugging option in the mobile.
7: Open the ADB Interface update driver.
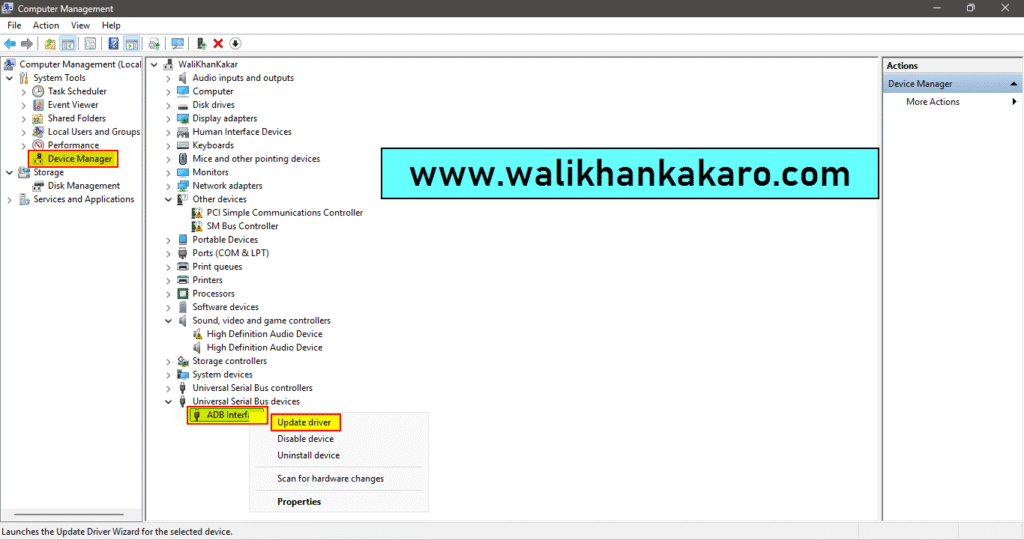
8: Click on the Browse my computer for drivers.
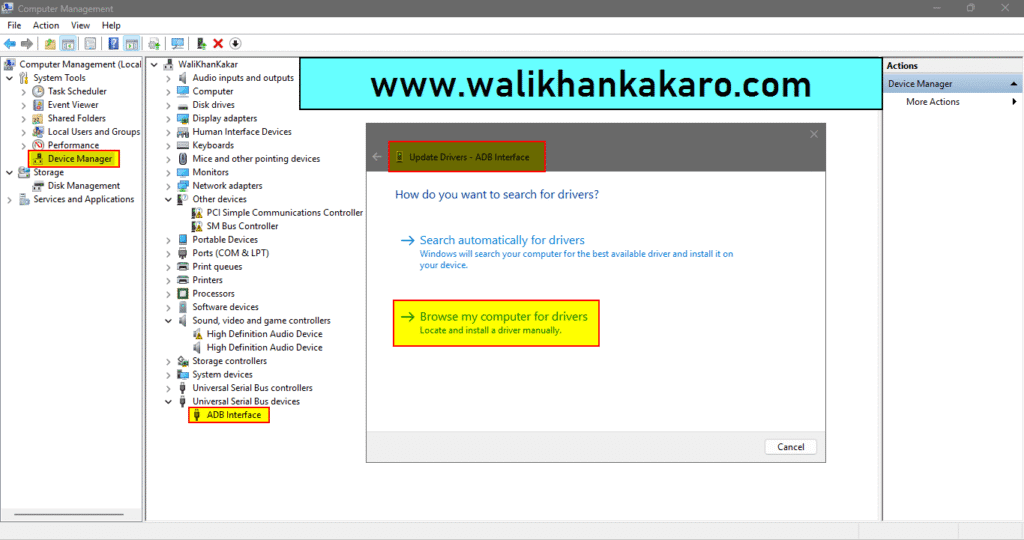
9: Click on the Let me pick from a list of available drivers on my computer.
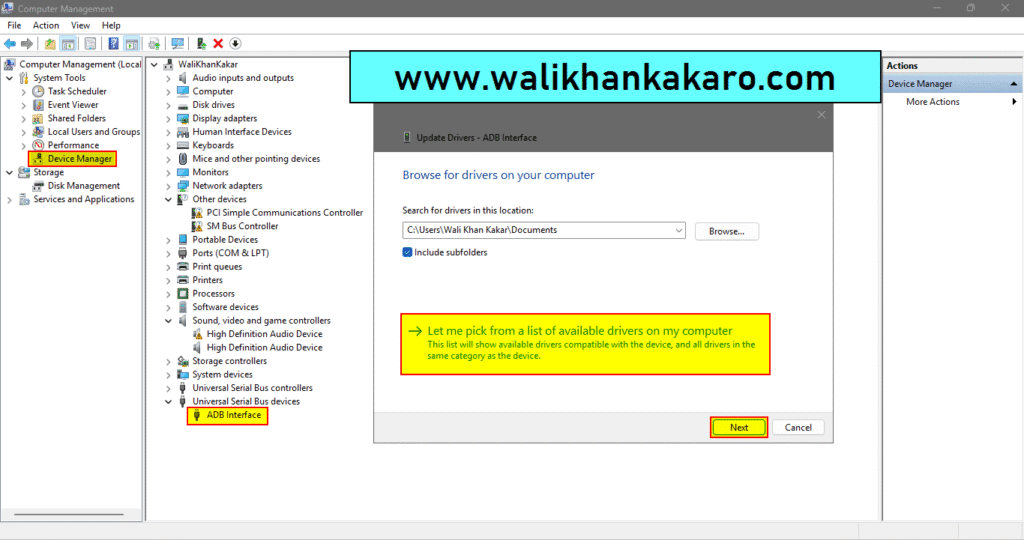
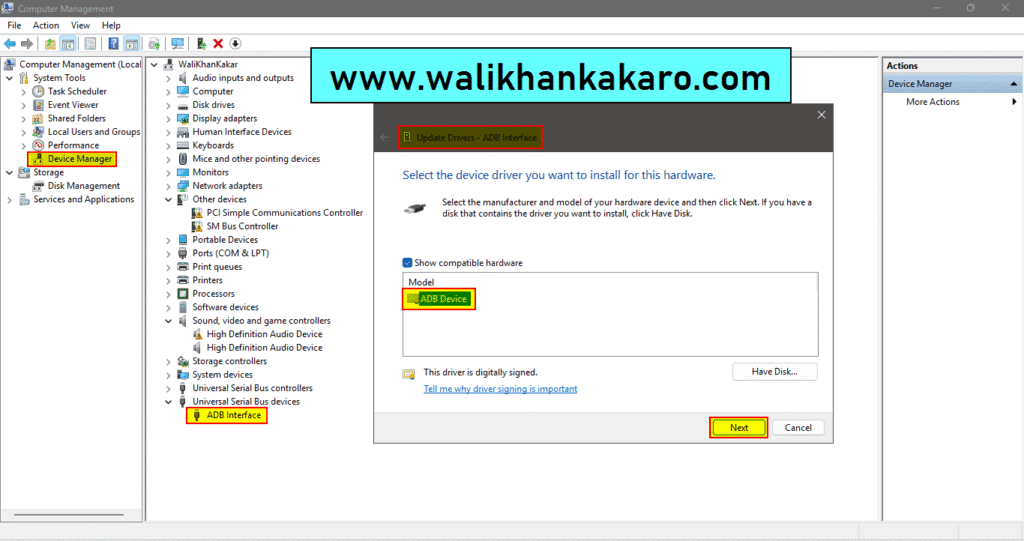
10: Select the ADB Device and install the drivers.
11: Open the Command Prompt.
Shortcutkey: Windows sign + R = cmd
12: Back up the directory in the Command Prompt.
Command: cd..
13: Back up the directory in the Command Prompt.
Command: cd..
14: Check the adb directory in the Command Prompt.
Command: dir
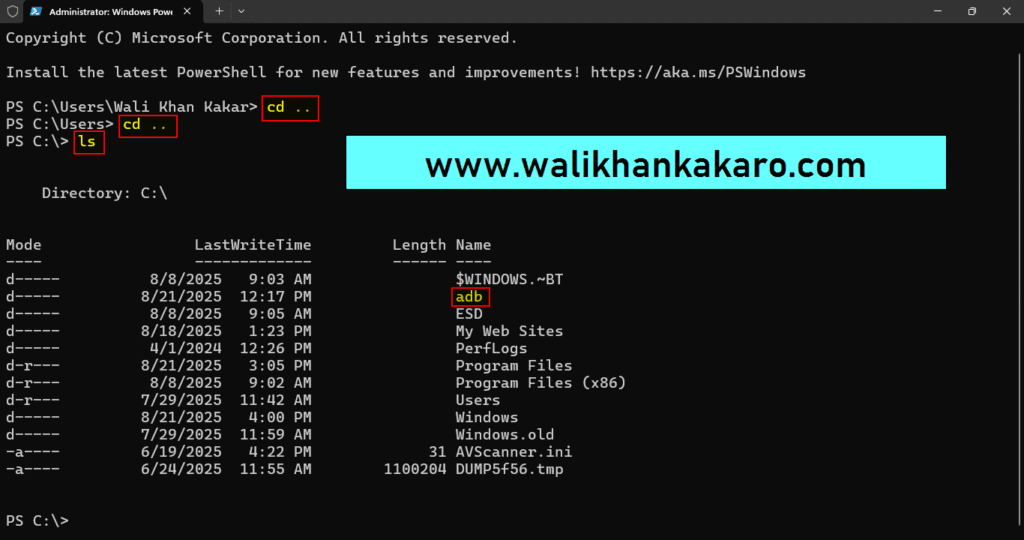
16: Go to the adb directory.
Command: cd adb
17: Then go to the platform-tools directory.
Command: cd platform-tools
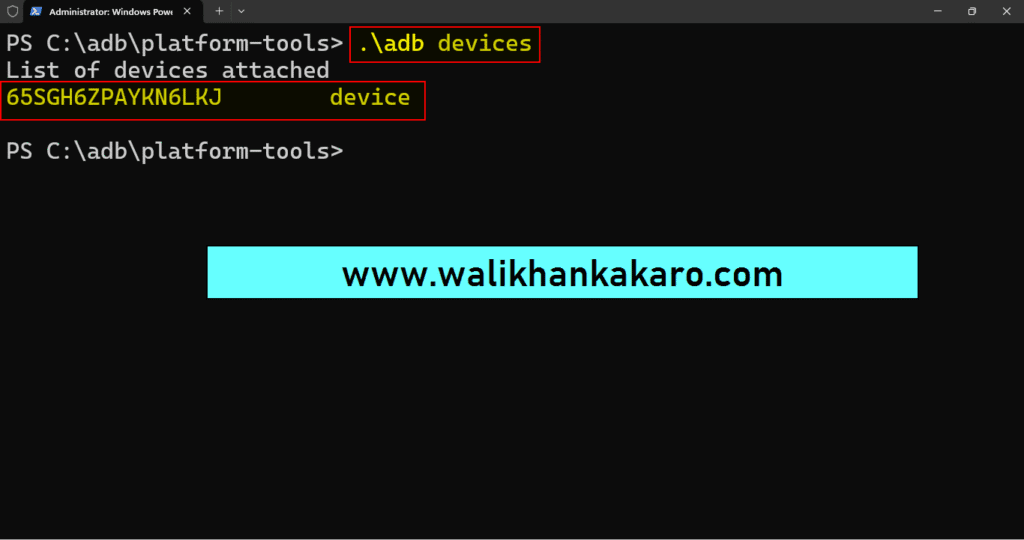
18: Check the adb devices.
Command: .\adb devices
19: Give the permissions when the notification comes into your mobile.
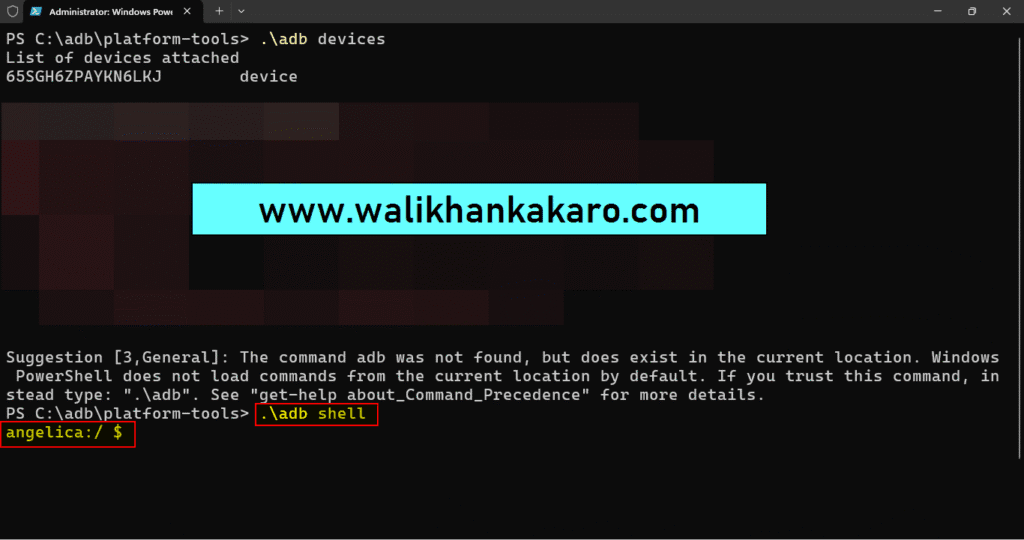
20: The devices are attached.
21: Access to the Shell.
Command: .\adb shell
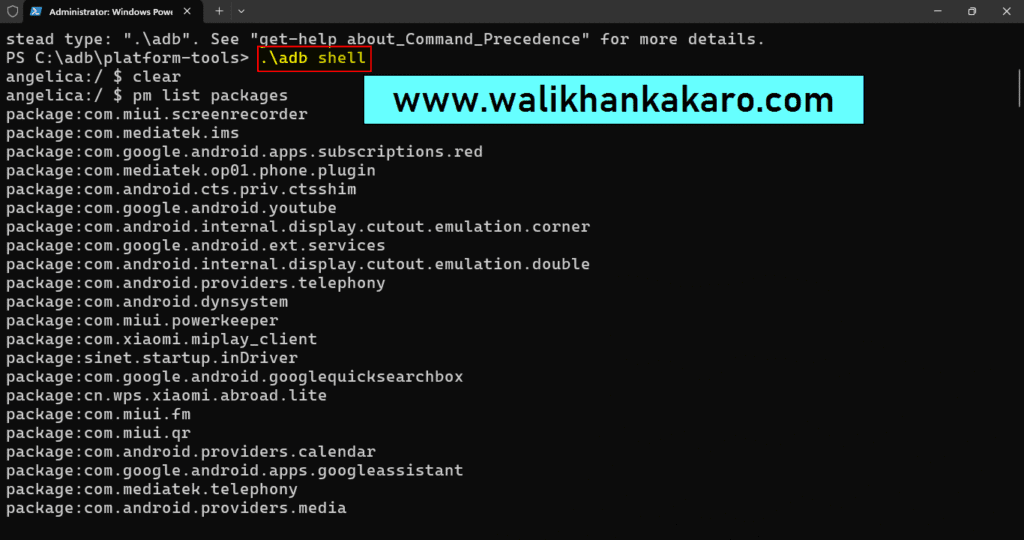
22: Check the packages.
Command: pm list packages
Api Testing
1: Download Postman.
Website: https://www.postman.com/downloads/
API testing demo websites free
1: httpbin.org.
Website: https://httpbin.org/#/
2: Dummy Rest API Example.
Website: http://dummy.restapiexample.com/
3: JSONPlaceholder.
Website: https://jsonplaceholder.typicode.com/
4: FakeRESTApi.
Website: https://fakerestapi.azurewebsites.net/index.html
5: REST API endpoints for repositories.
Website: https://docs.github.com/en/rest/repos?apiVersion=2022-11-28
6: API Platform.
Website: https://demo.api-platform.com/

API testing interview questions
1: What is API Security Testing?
Answer: API tests use extreme conditions and inputs when analyzing applications. This removes vulnerabilities and guards the app from malicious code and breakage. API tests can be integrated with GUI tests.
2: Software used for API testing.
Answer: Postman and Burp Suite.
How to find bugs in an Android phone
1: Download the Yaazhini software.
Website: https://www.vegabird.com/yaazhini/

2: Install the Yaazhini software.
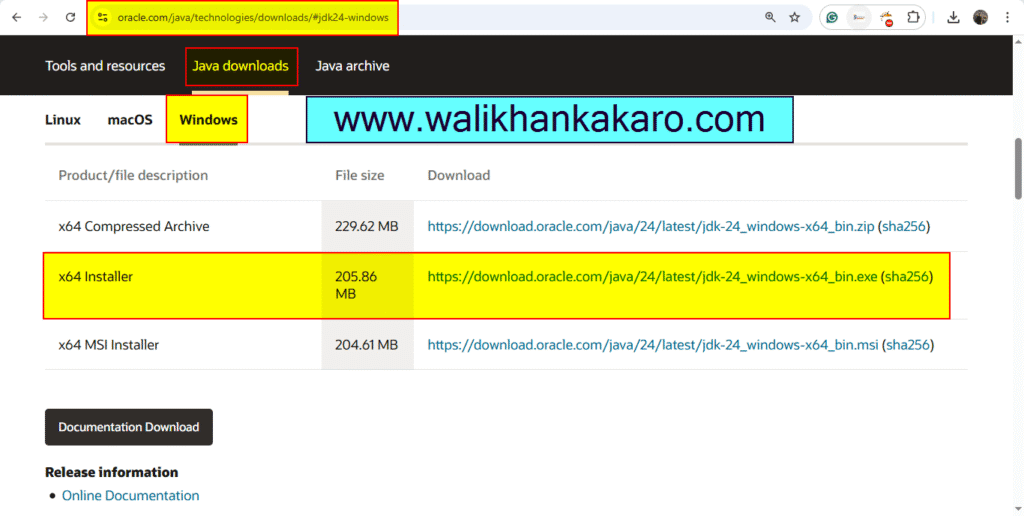
3: Also install the JDK.
Website: https://www.oracle.com/java/technologies/downloads/
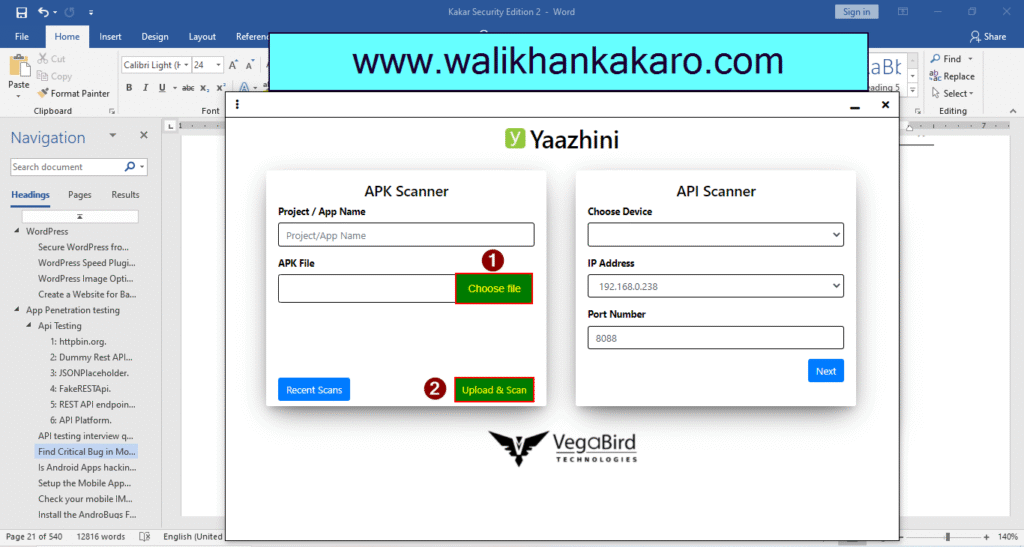
4: Upload the APK file and start the scan.
Mobile Security Framework
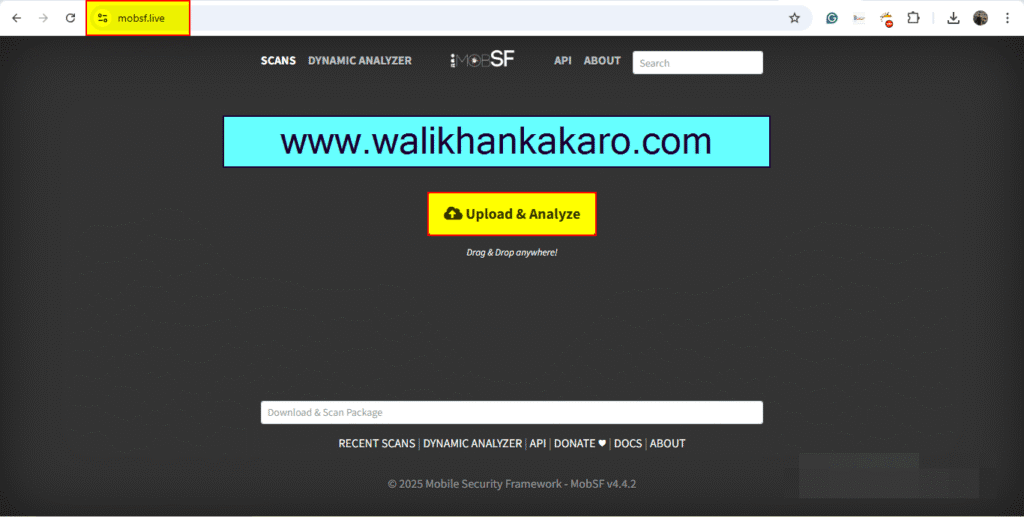
1: Open the MobSF (Mobile Security Framework) website.
Website: https://mobsf.live/
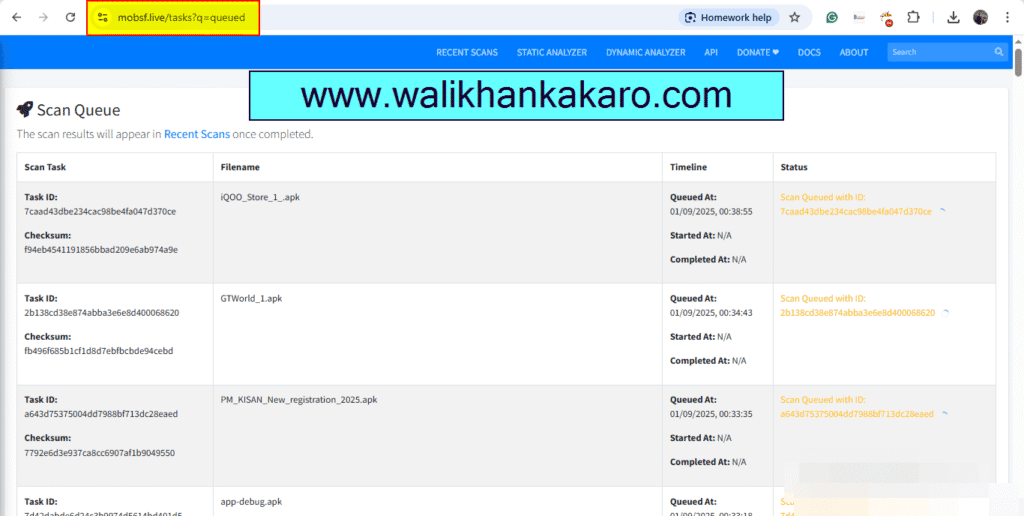
2: Scan the App.
3: Download the PDF Report.
Set up the mobile app pentesting labs APK
1: Download Genymotion.
Website: https://www.genymotion.com/product-desktop/download/
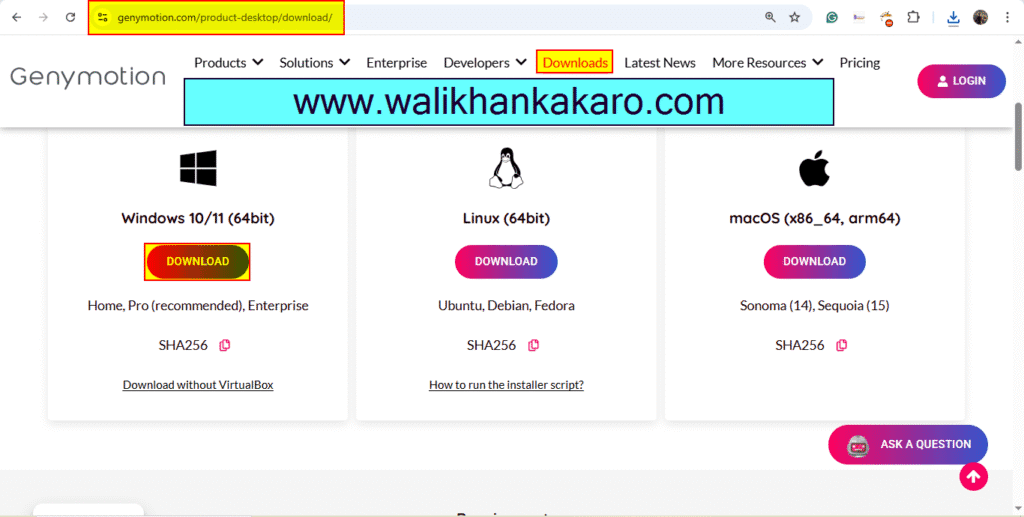
2: Install Genymotion.
3: Create the Genymotion account.
Website: https://www-v1.genymotion.com/account/create/
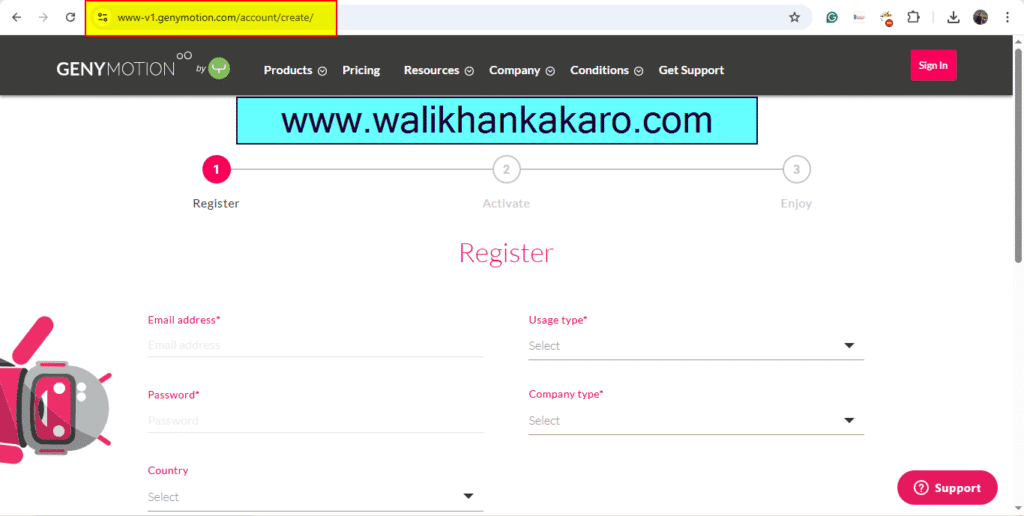
4: Check the Gmail account and activate the Genymotion account.
5: Open the Genymotion software.
6: Log in to a Genymotion account.
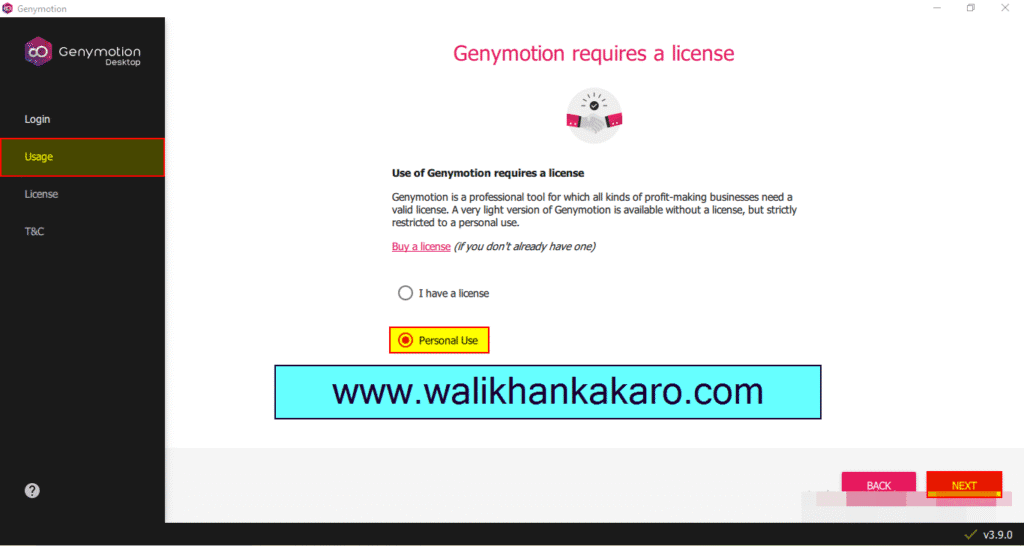
7: Select the Personal Use.
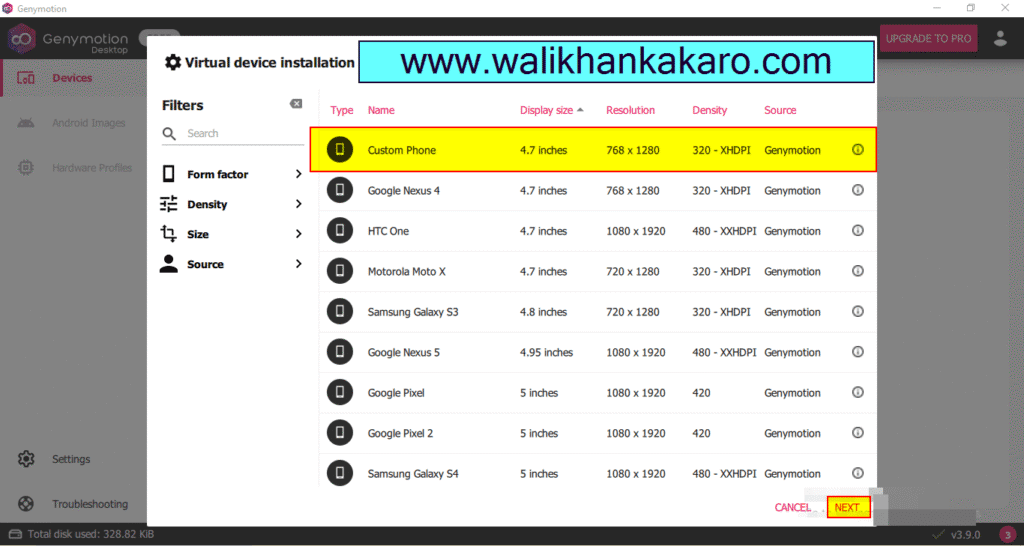
8: Add the Virtual Device.
Shortcut key: Ctrl + n
9: Install the Custom Phone.
APK file online scanning
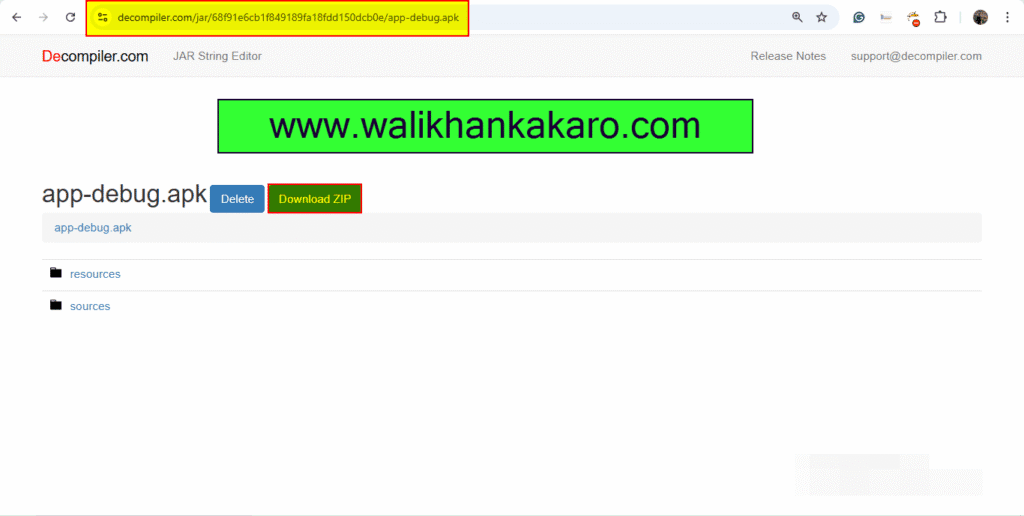
1: Scan the APK file online with the help of a Java decompiler.
Website: http://javadecompilers.com/

2: Download the scanned APK file zip.
AndroBugs Framework
1: What is AndroBugs Framework?
Answer: The AndroBugs Framework is an Android vulnerability analysis system that helps developers and hackers identify potential security vulnerabilities in Android applications. No splendid GUI interface, but the most efficient (less than 2 minutes per scan on average) and more accurate.
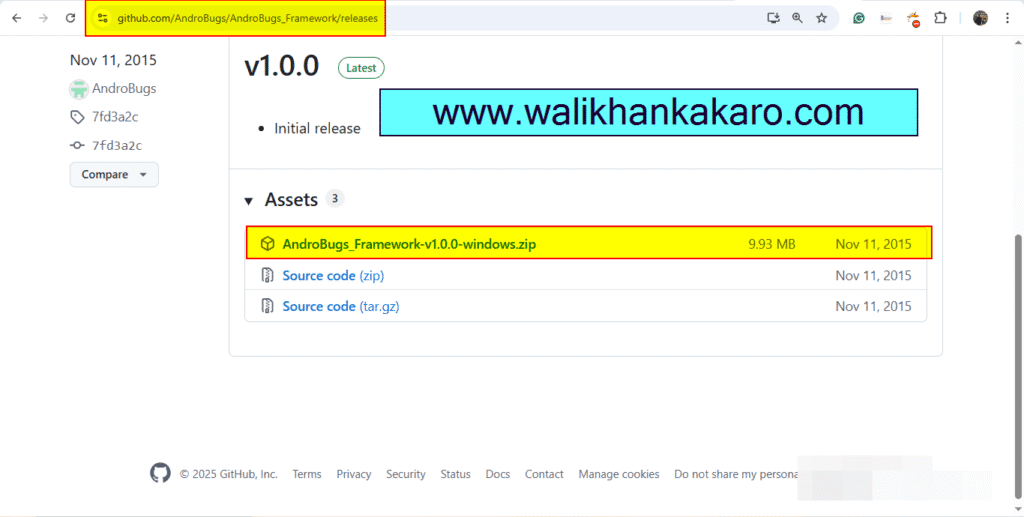
2: Download the AndroBugs Framework.
Website: https://github.com/AndroBugs/AndroBugs_Framework/releases
3: Make a folder in the Disk where you want to install with the name of AndroBugs Framework.
4: Copy the AndroBugs Framework and paste it into the AndroBugs Framework folder.
5: Unzip the AndroBugs Framework folder.
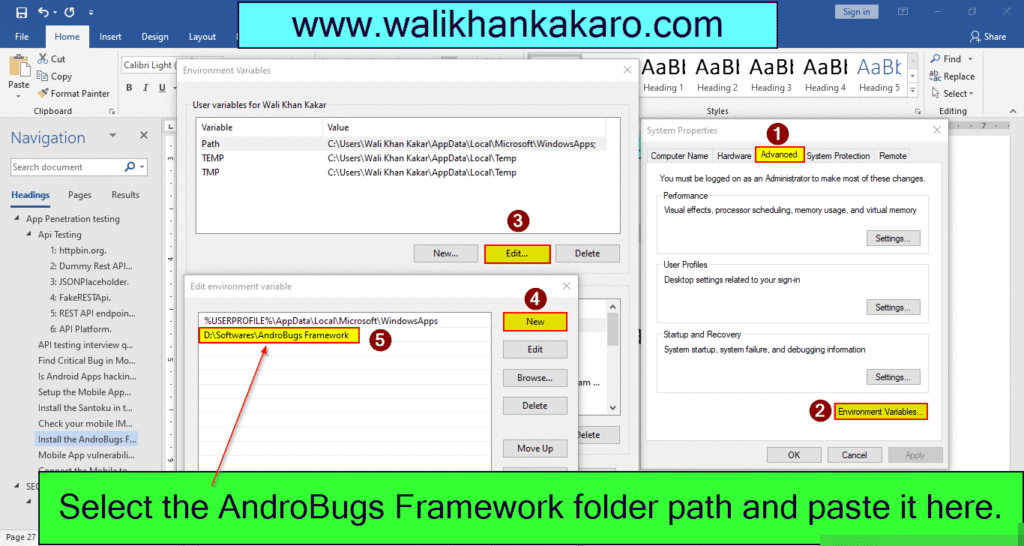
6: Open the Search Bar and go to the Environment Variables.
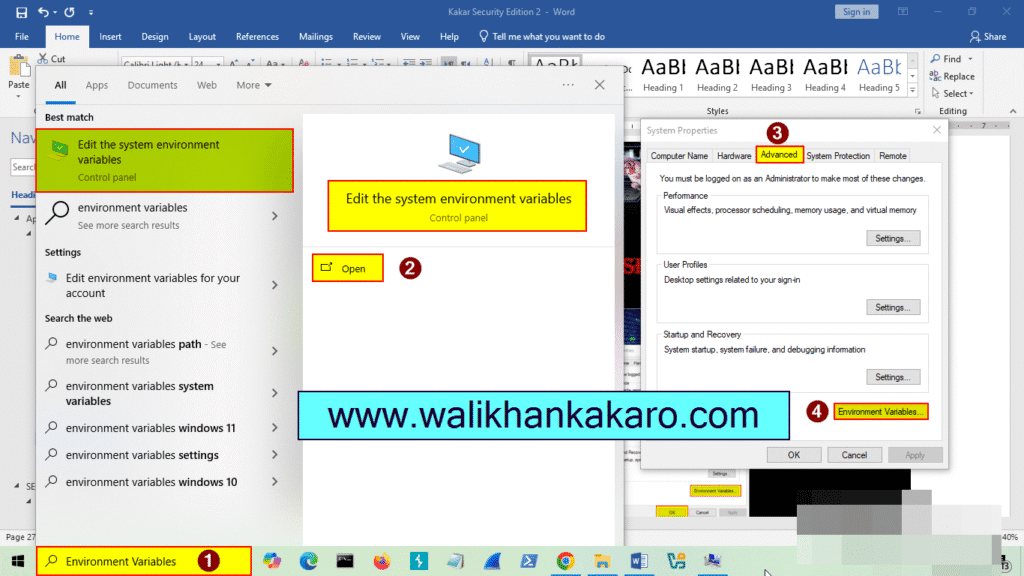
7: Add the Environment Variables of the AndroBugs Framework.
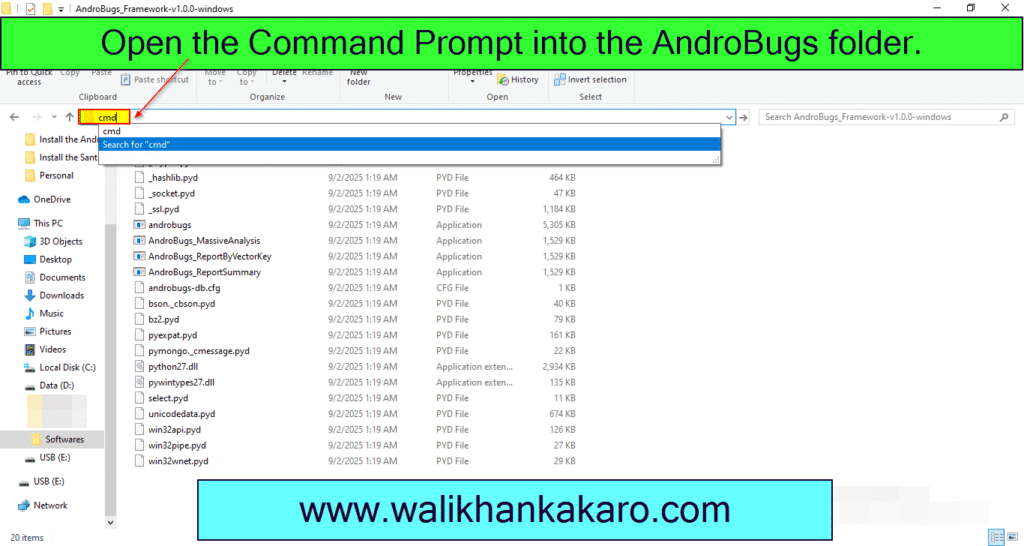
8: Run the AndroBugs Framework with the help of the Command Prompt.
9: Check the AndroBugs Framework help.
Command: androbugs.exe -h
10: Copy your APK file and paste it into the AndroBugs Framework folder.
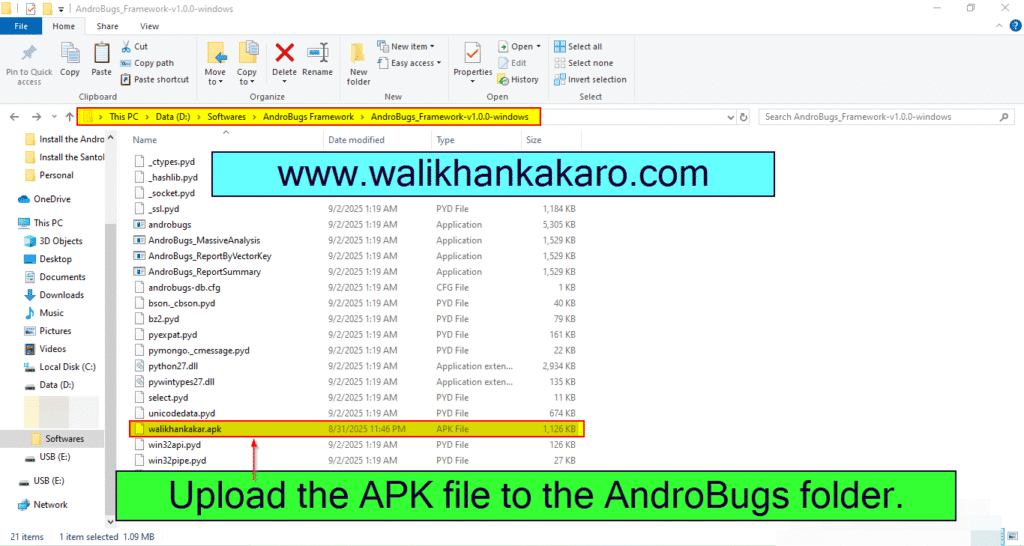
11: For the testing, download this vulnerable APK file.
Website: https://github.com/dineshshetty/Android-InsecureBankv2
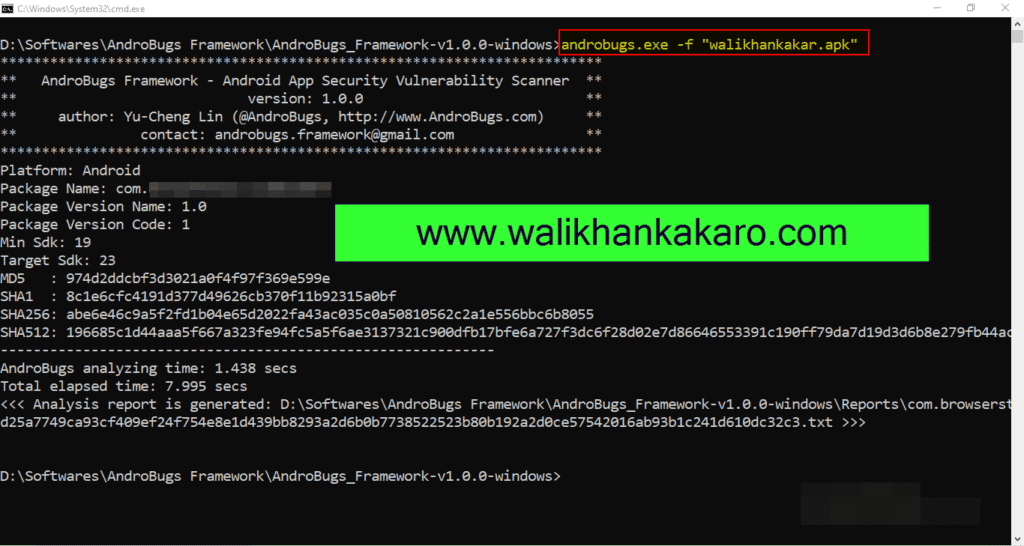
12: Scan the APK file.
Command: androbugs.exe -f “walikhankakar.apk”
13: Check the scanned APK file report in the AndroBugs Framework folder.
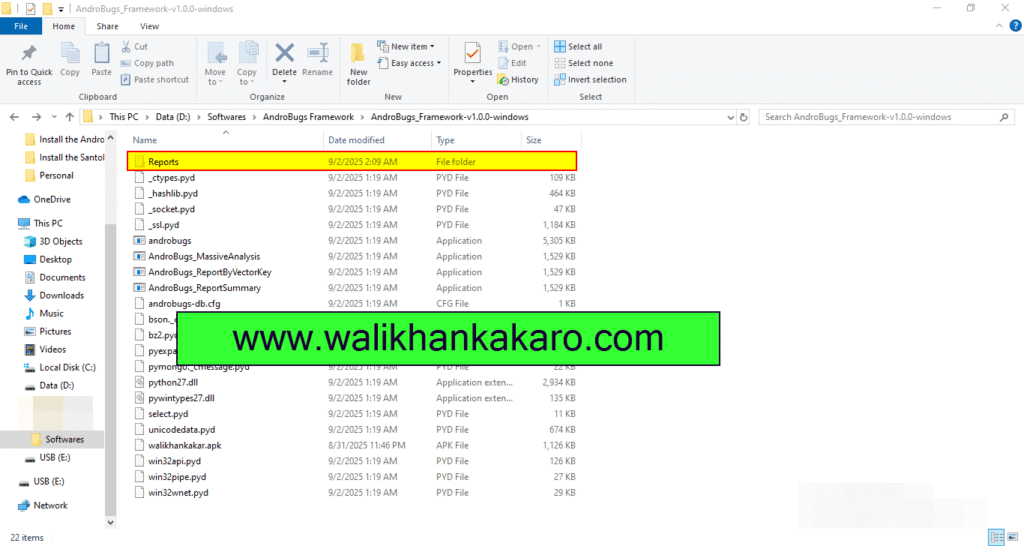
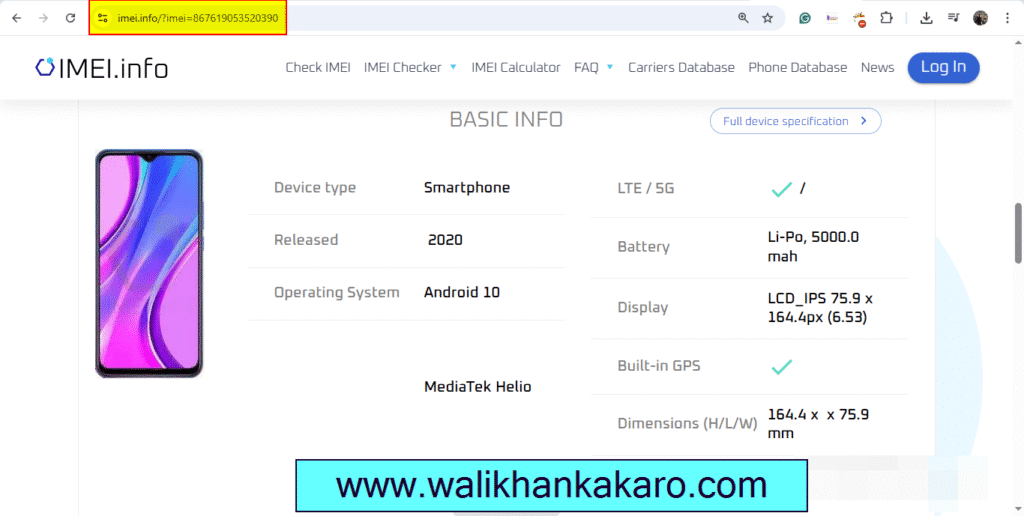
Check your mobile IMEI details online for free
1: Check your Mobile IMEI numbers.
Code: *#06#
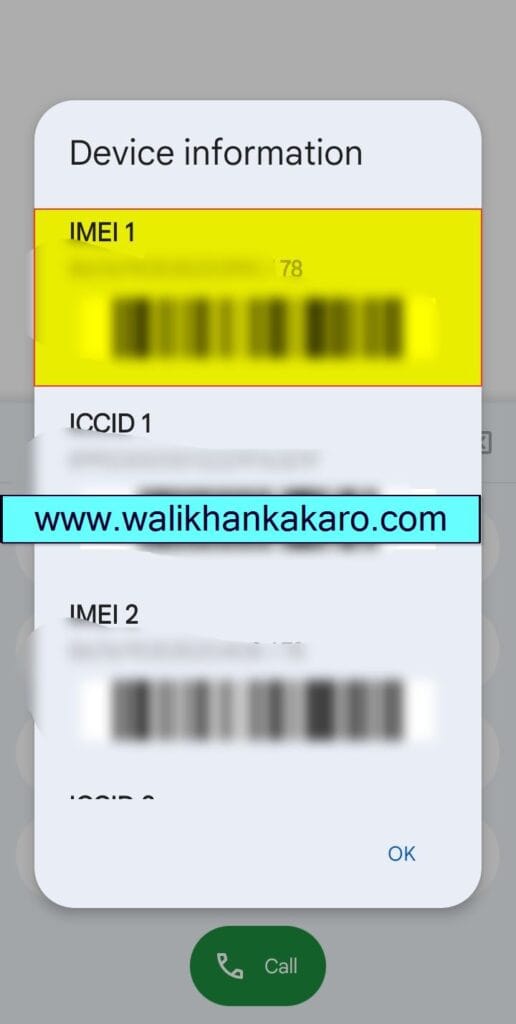
2: Copy the IMEI numbers and paste them.
Website: https://www.imei.info/

3: Here are your IMEI number details.