Table of Contents
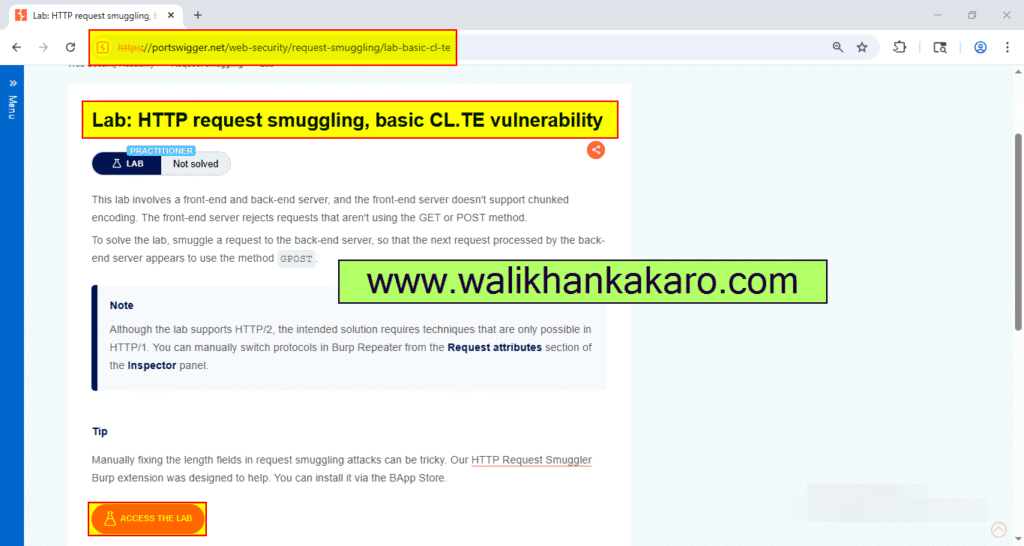
HTTP request smuggling, basic CL.TE vulnerability
1: Open the Burp Suite.
2: Access the Lab HTTP request smuggling, basic CL.TE vulnerability.
Website: https://portswigger.net/web-security/request-smuggling/lab-basic-cl-te
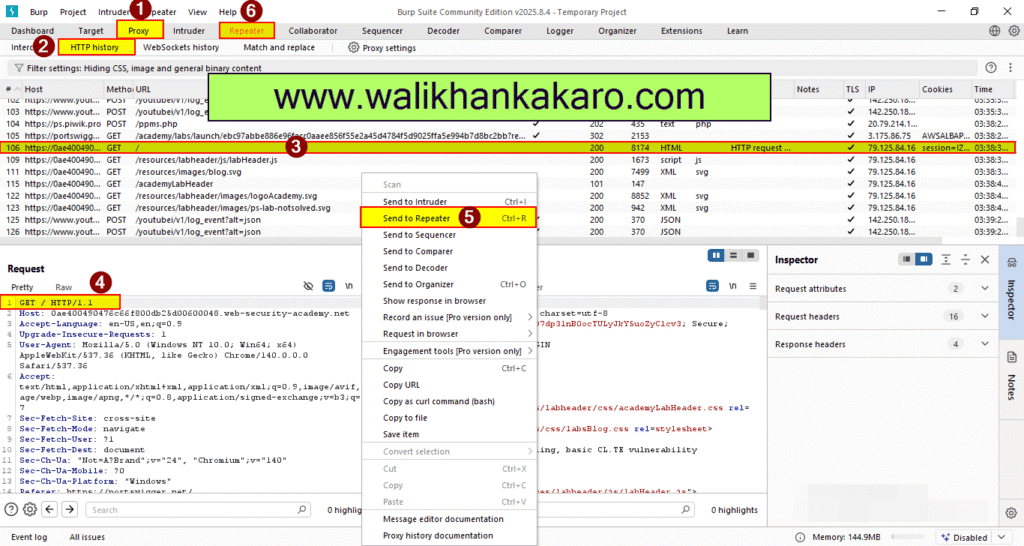
2: Send a request to the Repeater.
Shortcut: Ctrl + R
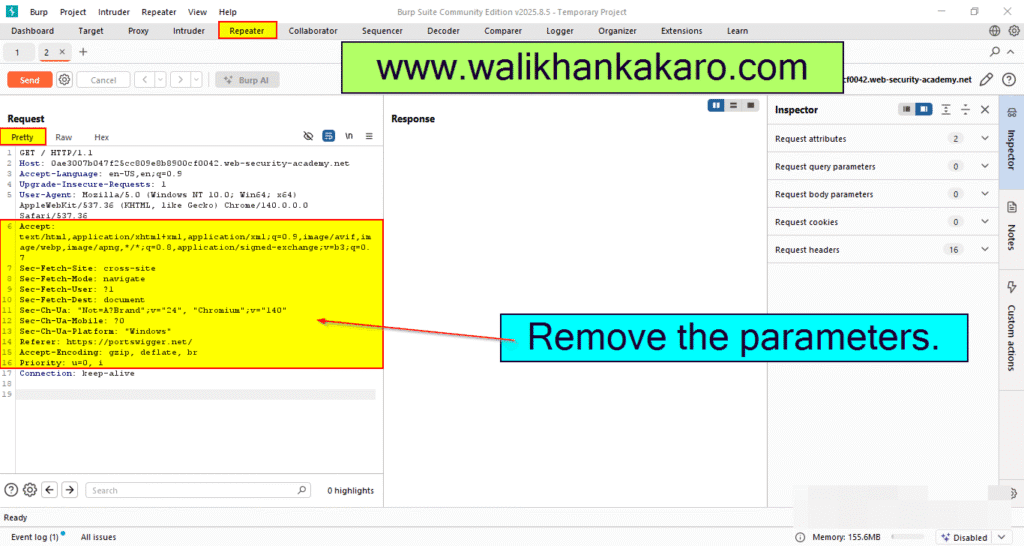
3: Remove the parameters.
4: Change the Parameters.
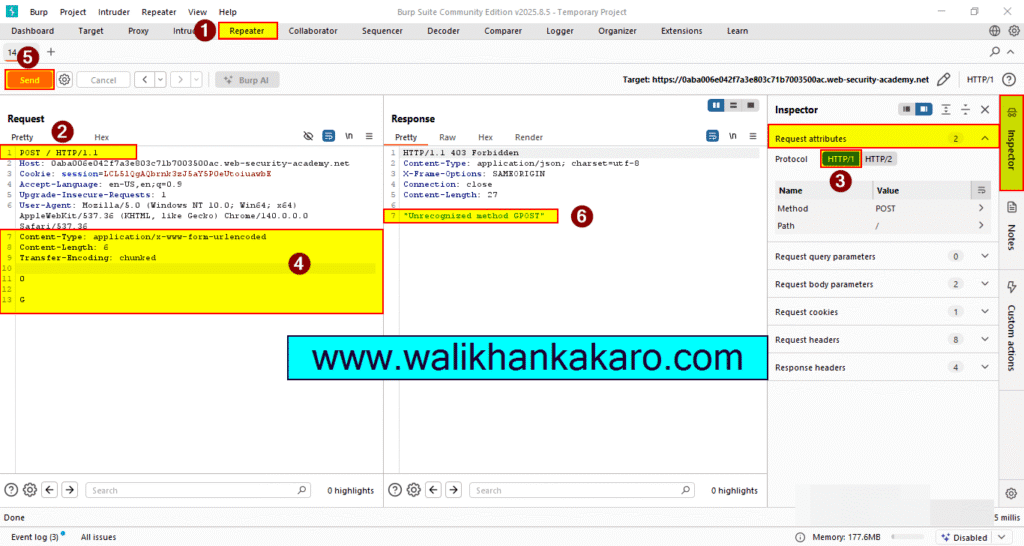
5: Send the request three times.
6: Your lab has been completed.



