Table of Contents
XSS session cookie
1: Open the demo.testfire the website in Chrome.
Website: https://demo.testfire.net/login.jsp
Username: admin
Password: admin
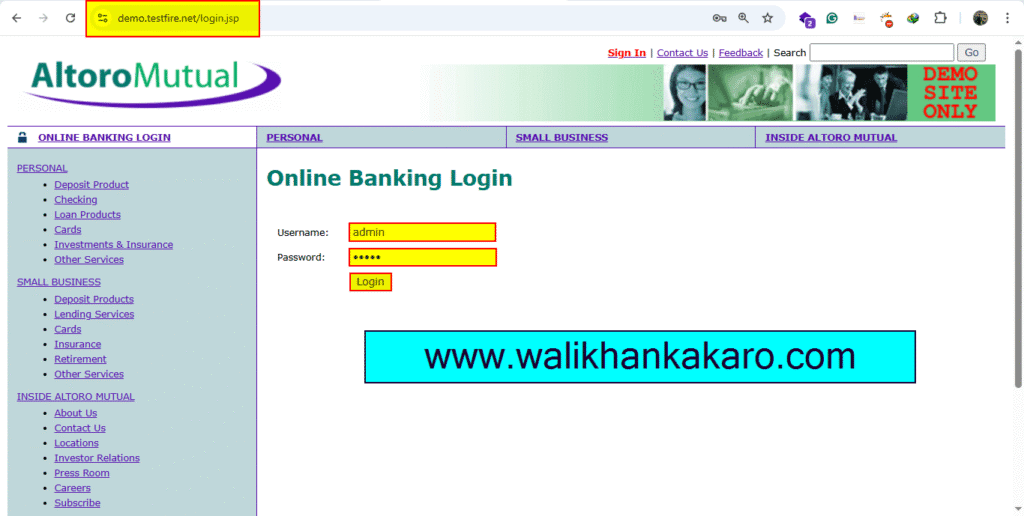
2: Don’t log in.
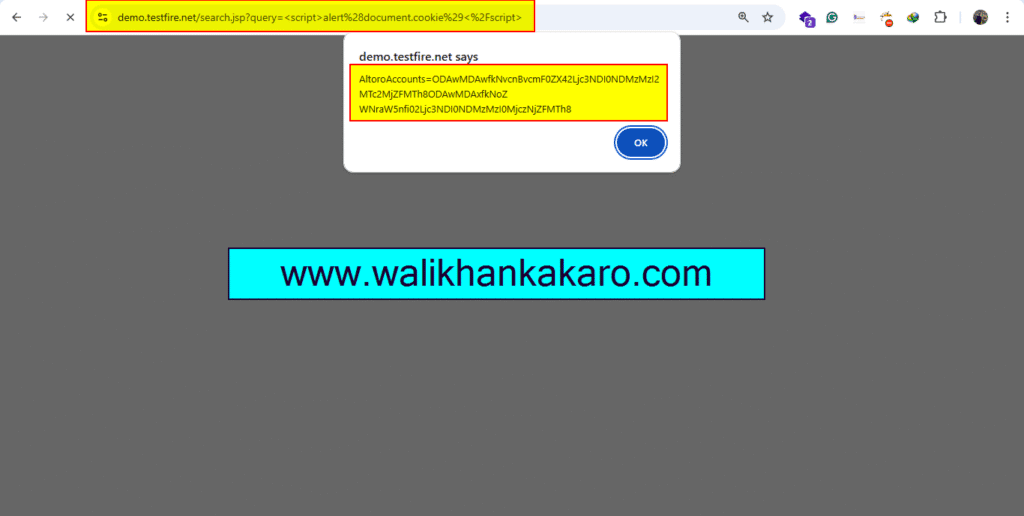
3: Check the cross-site scripting (XSS) vulnerability in the Website’s Search Bar.
XSS Payload: <script>alert(document.cookie)</script>
4: Cross-Site Scripting (XSS) cookie Session ID Vulnerability works when you log into the system.
5: Cross-Site Scripting (XSS) cookie Session ID Vulnerability.
Note: Without logging into the system, it doesn’t work.
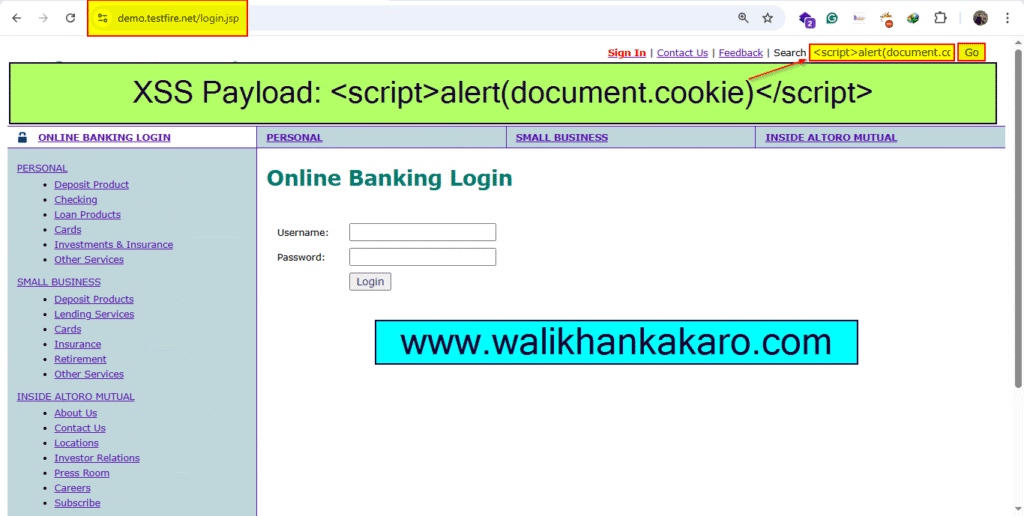
6: Now log into the system and inject the XSS payload.
7: Paste the XXS Payload into the website on the search tab.
XSS Payload: <script>alert(document.cookie)</script>
8: Here is the Session ID.