Table of Contents
Secure the Computer from the Black Hat Hacker
1: Go to the Windows Defender Firewall with Advanced Security.
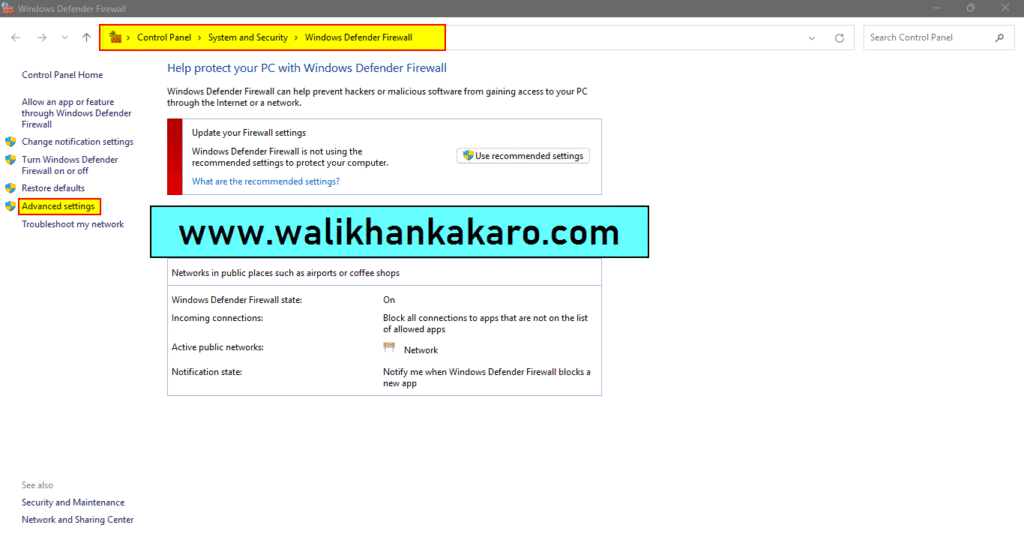
2: Open the Inbound Rules.
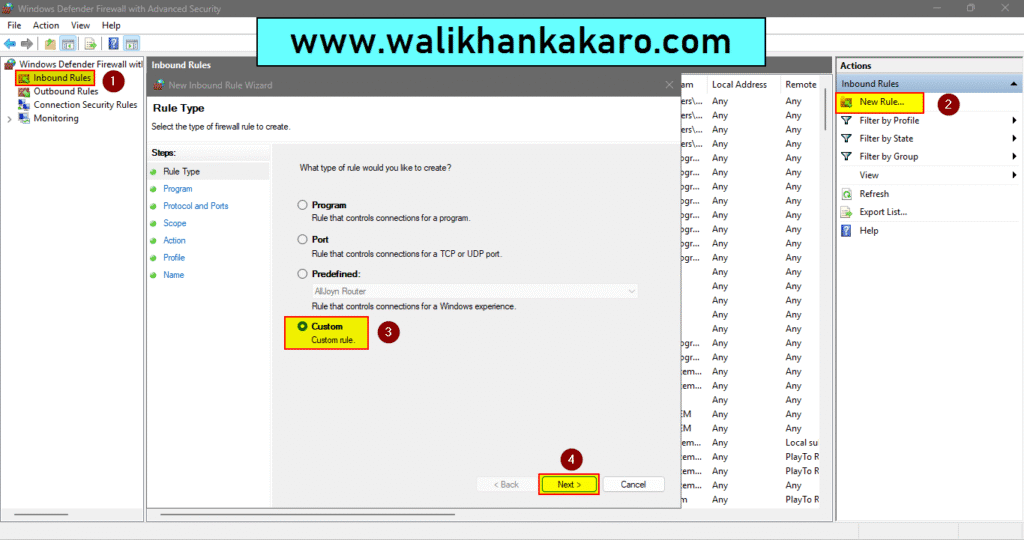
3: Create the New Rule.
4: Go to the custom rule.
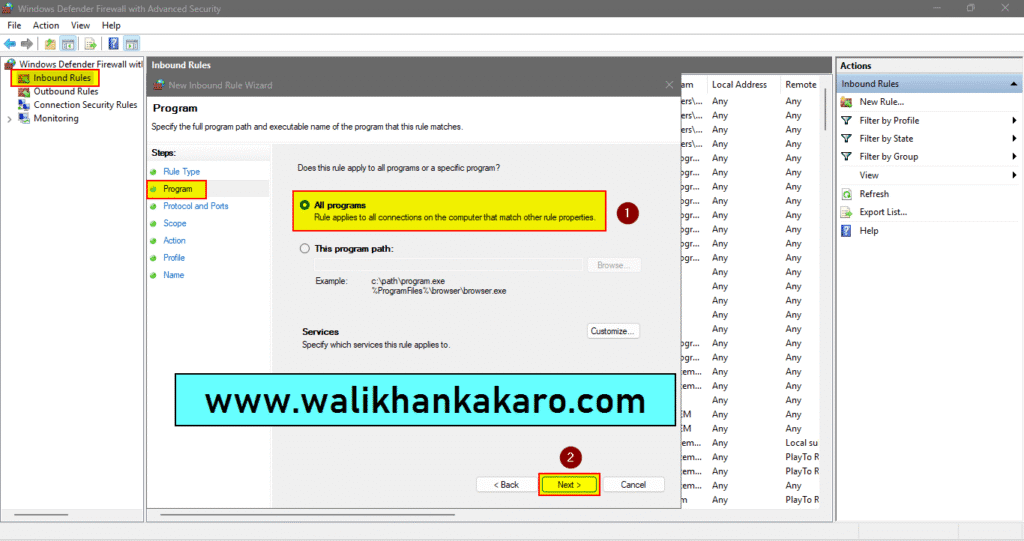
5: Next to the All programs.
6: What is ICMP?
Answer: The Internet Control Message Protocol (ICMP) is a protocol that devices within a network use to communicate problems with data transmission.
7: Select the ICMPv6 Protocol.
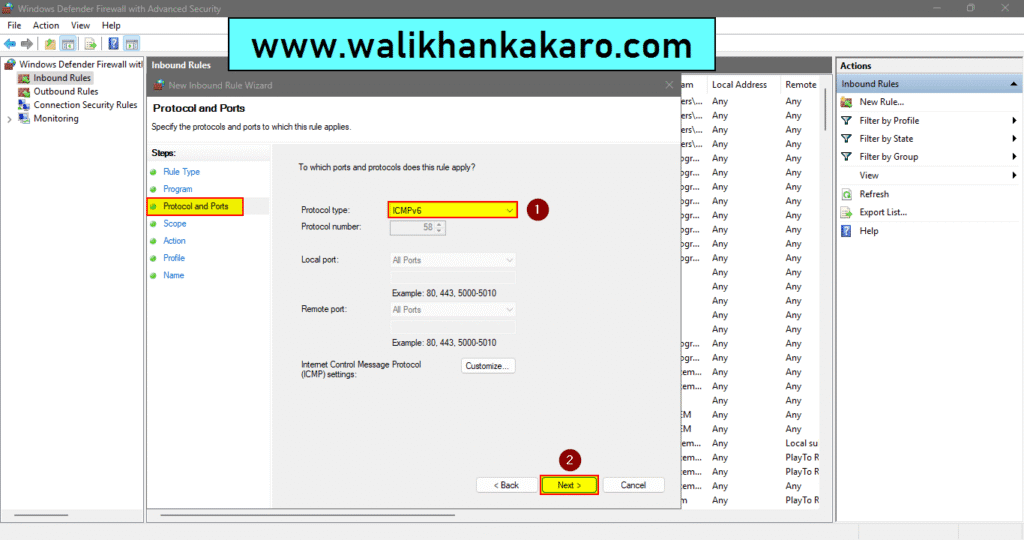
8: Follow the instructions.
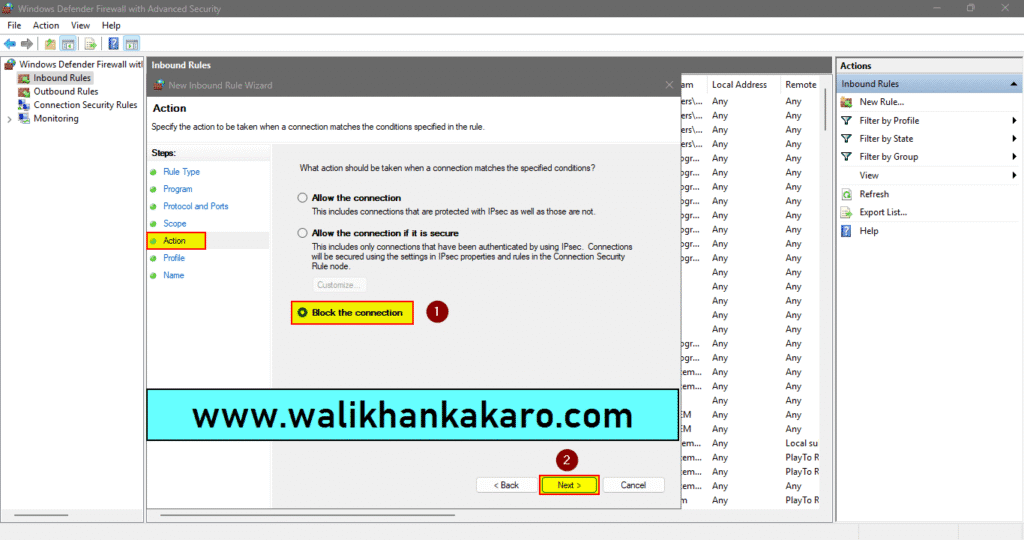
9: Block the connection.
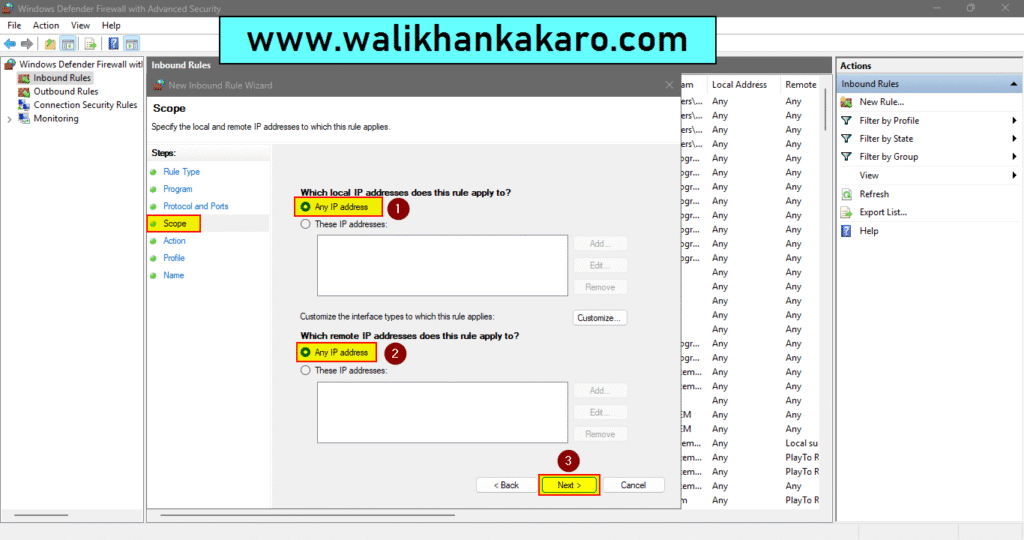
7: Apply rules to all.
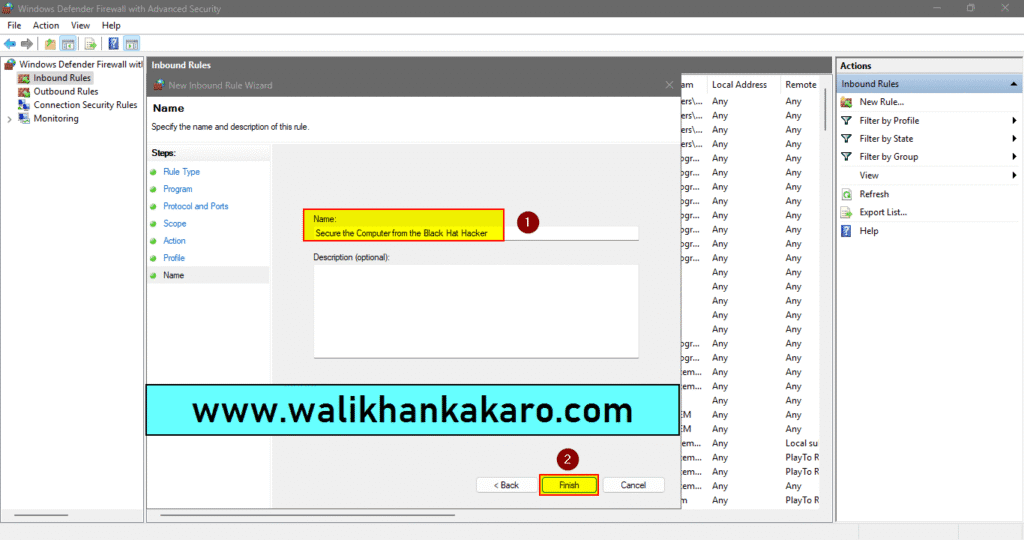
8: Give the rule name.
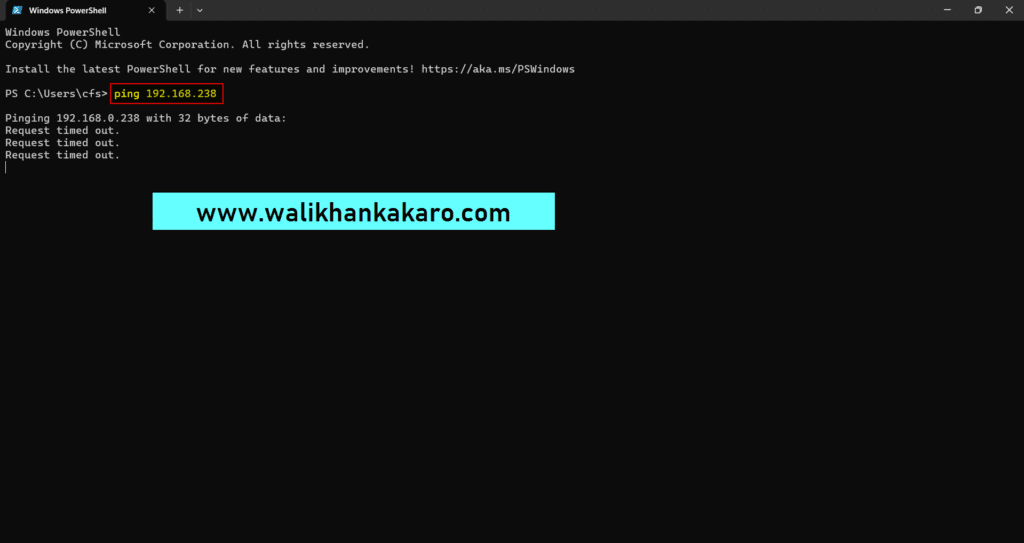
9: Ping your computer IP Address in the Command Prompt.
Command: ping 192.168.43.126
10: Know its work.